Endpoint security and the rise of Managed Device Services
CIO
MARCH 6, 2024
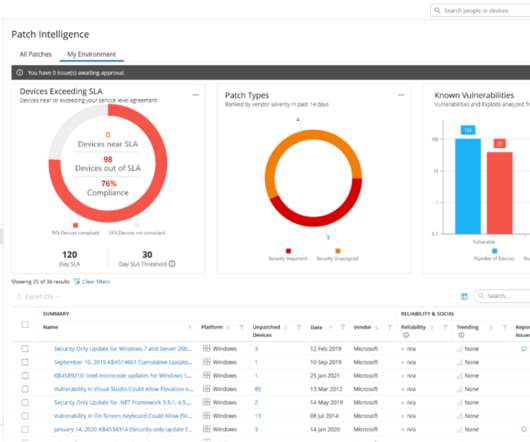
Despite growing interest in “as a service” consumption models for everything from infrastructure to storage, most enterprises have continued to procure, maintain, and manage endpoint devices in-house. Security is a key driver. In this environment, endpoint security becomes increasingly important.





















































Let's personalize your content