5 ways to maximize your cloud investment
CIO
JANUARY 10, 2024
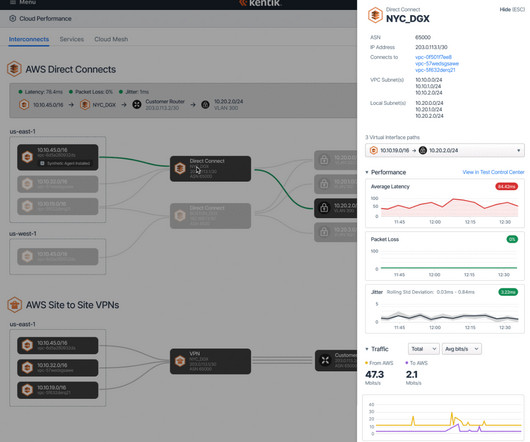
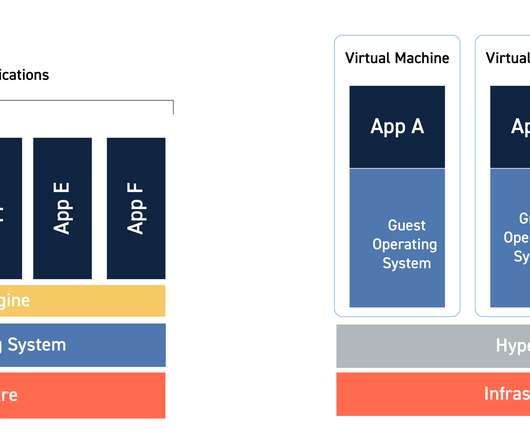
No IT organization wants to get caught short on processing or storage resources that could negatively affect operations, or have to suddenly add resources that exceed the budget. For example, organizations may commit to containers that are too large, or reserve too much disk space.









































Let's personalize your content