TDD and System Architecture
Net Objectives
APRIL 3, 2019
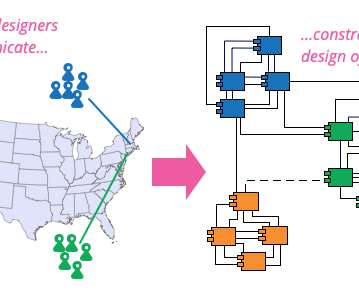
When first adopting TDD, developers can run into some roadblocks that seem to indicate that TDD is a difficult process. In truth, some of these problems actually indicate faults in the system architecture.











































Let's personalize your content