Advantages and Disadvantages of Firewall in Computer Network
The Crazy Programmer
OCTOBER 6, 2021
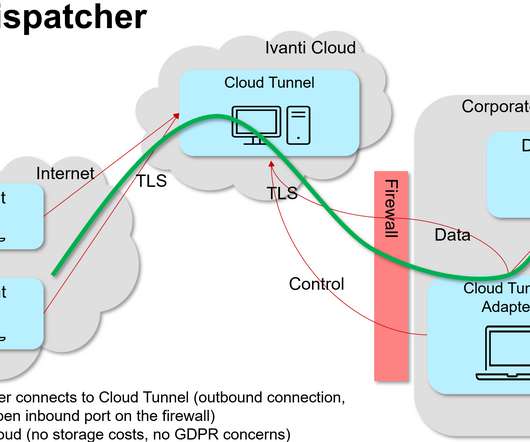
The computer connected with the internet can be more likely to get affected by viruses and cyber-attacks. Nowadays, the firewall is used mainly in organizations and also by individuals. But do you know what type of advantages users get after installing a firewall on their computer? What is Firewall in Computer Network?


















































Let's personalize your content