A Practical History of the Firewall – Part 1: Early Days
Firemon
APRIL 9, 2024
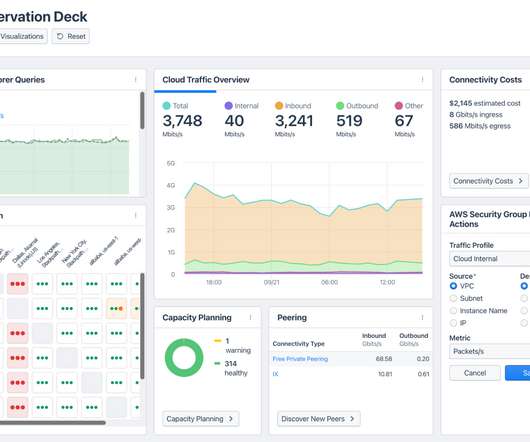
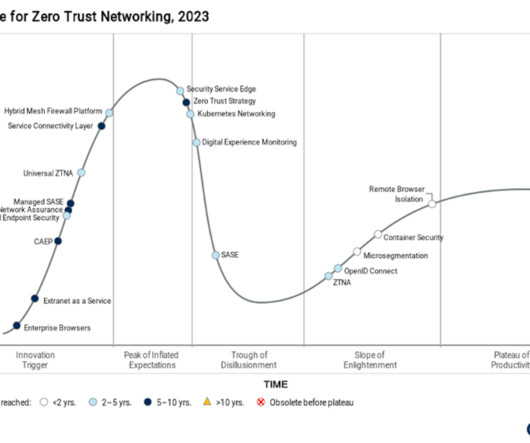
Jody Brazil CEO at FireMon This is not a primer on firewalls, nor is it meant to represent a comprehensive picture of the history of the firewall. There are plenty of good resources that outline the history of the firewall, for example Wikipedia: [link]. On this front, stateful inspection won.




















































Let's personalize your content