First-Ever Attack Leveraging Kubernetes RBAC to Backdoor Clusters
Aqua Security
APRIL 21, 2023
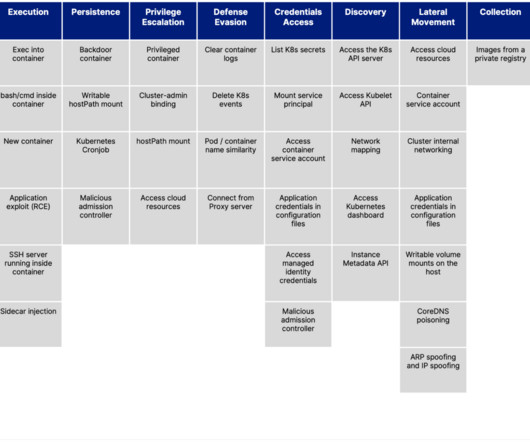
We have recently discovered the first-ever evidence that attackers are exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) in the wild to create backdoors. The attackers also deployed DaemonSets to take over and hijack resources of the K8s clusters they attack.















































Let's personalize your content