Cloudy with a chance of threats: Advice for mitigating the top cyber threats of 2024
Lacework
FEBRUARY 7, 2024
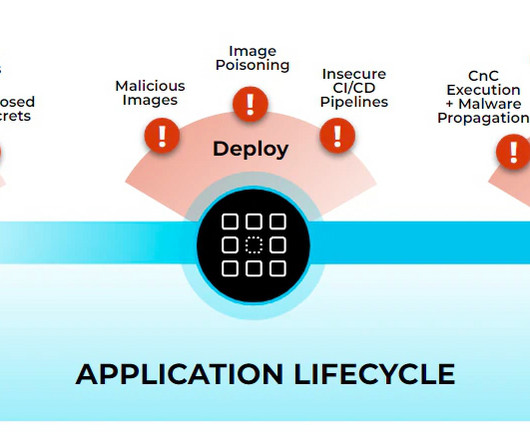
Securing the cloud is a race against time. Developers are building systems and applications faster than ever, but this creates more risks and vulnerabilities for hackers to exploit. As security researchers, we’re constantly analyzing and anticipating cyber threats. Who’s behind the threats?

















































Let's personalize your content