Increase customer protection with edge security
CIO
APRIL 5, 2023
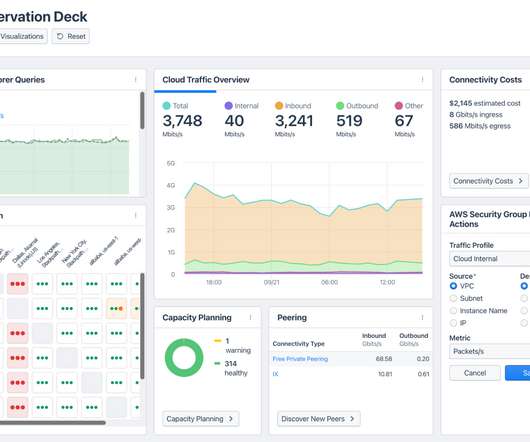
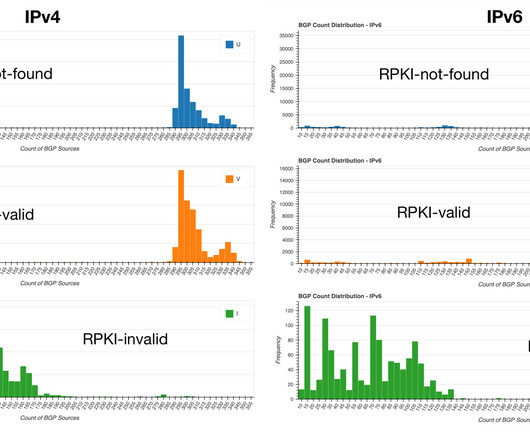
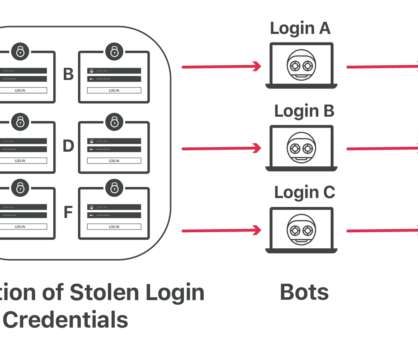
Traditional IT security methods are increasingly flawed and the volume and sophistication of threats continue to increase. New security methods delivered at the edge of the network, closer to the customer, are emerging as a more effective method for combating the increase in security threats.













































Let's personalize your content