Expel raises $140.3M Series E for its managed threat detection and response platform
TechCrunch
NOVEMBER 18, 2021
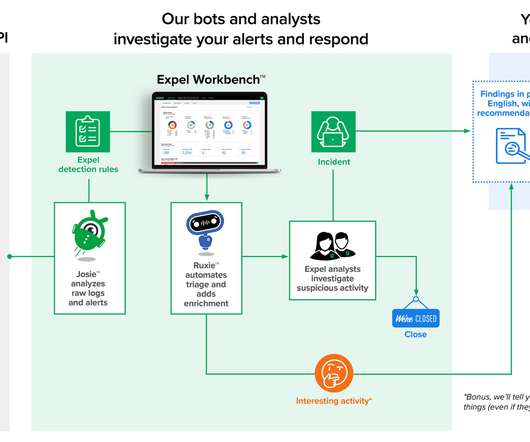
Cybersecurity platform Expel , which specializes in threat detection and response, today announced that it has raised a $140.3 By building what the company calls an “automation-forward” system, its systems are able to quickly react to potential issues.


















































Let's personalize your content