Comprehensive Exploration on Understanding Datadog
Perficient
DECEMBER 21, 2023
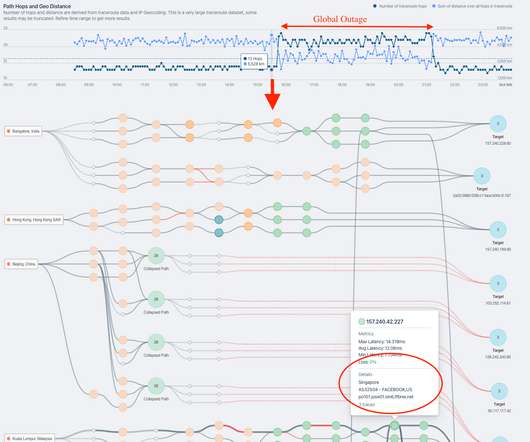
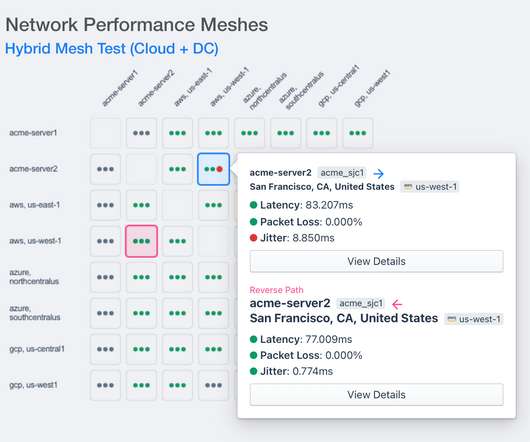
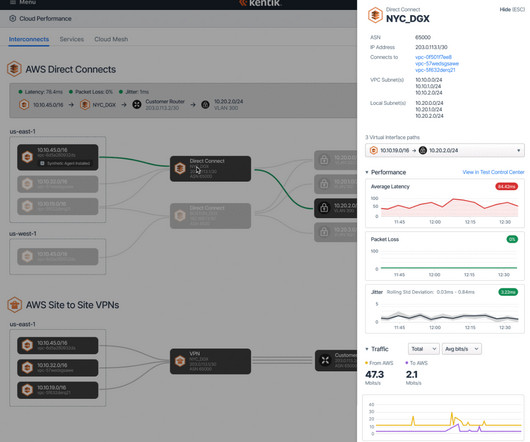
APM & Continuous Profiler Datadog’s Application Performance Monitoring (APM) offers deep insights into application performance. Automatically generated dashboards and detailed traces of individual requests empower users to monitor key metrics like request volume and latency.


















Let's personalize your content