Cloud Security: Improve Cyber Hygiene with Resource Tagging
Tenable
JANUARY 28, 2021
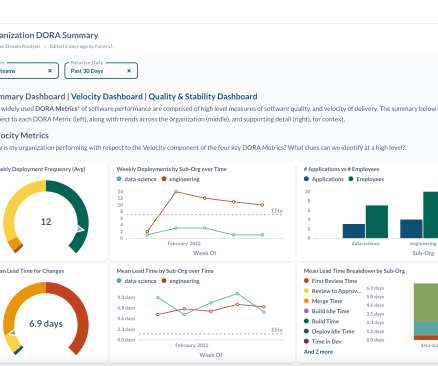
Adopting consistent tagging practices can help to quickly identity resources, ensure change control efforts, and reduce security risks within your cloud environments. As cloud footprints continue to scale, containing cloud costs and ensuring resource asset management have become top priorities. Why Tagging? But where do you begin?

















































Let's personalize your content