What are the main challenges CISOs are facing in the Middle East?
CIO
FEBRUARY 23, 2024
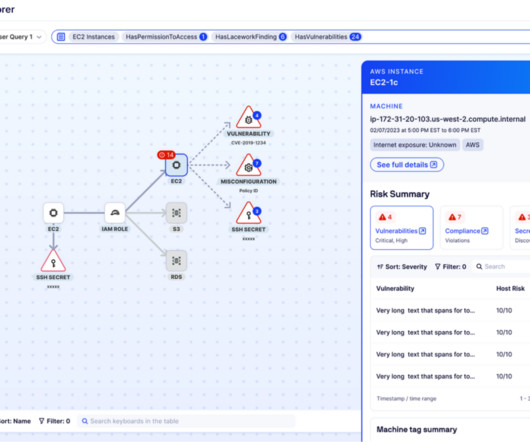
This continued emergence of cloud environments has greatly affected application development and their associated security architectures. Cloud environments by their nature often consist of rapid DevOps cycles eliminating the need for application developers to adequately maintain secure applications.


















































Let's personalize your content