4 core software security problems—and what to do about them
TechBeacon
OCTOBER 15, 2021
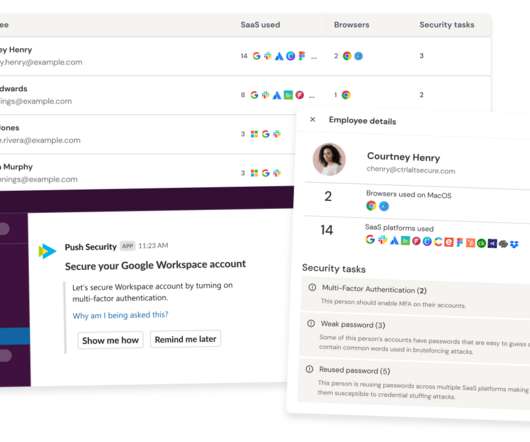
What’s worse, recent research from Stanford University Professor Jeff Hancock and security firm Tessian found that 88% of breaches are caused by human error. In 2020, in the US alone, more than 37 billion records were exposed in nearly 4,000 reported data breaches.



















































Let's personalize your content