Using Docker – Multiple Virtual Machines
Perficient
FEBRUARY 8, 2023
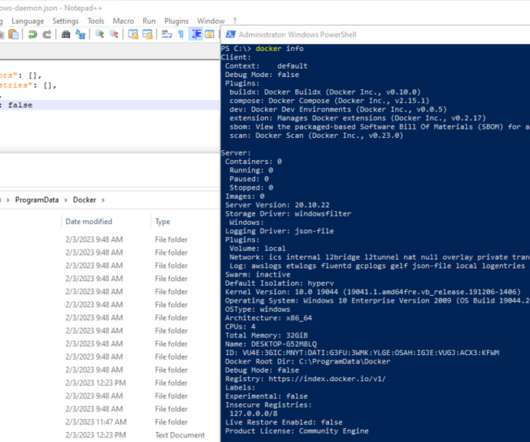
To accomplish this, I have a separate virtual machine for each client. When I complete a client project, I simply delete the virtual machine. There has to be a better way! Let’s create a new virtual drive that we can share between virtual machines and tell docker to store its data in the shared drive.















































Let's personalize your content