Security and Privacy of COVID-19 Contact-Tracing Apps
Symantec analyzed the top 25 COVID-19 national contact-tracing apps to see which follow security and privacy best practices.
Unfortunately, in this new COVID-19 era it’s not just our computers we have to protect from infection, but also ourselves and our loved ones. Along with social distancing, wearing a mask, and washing our hands, technology is also playing a part in the fight against the pandemic. COVID-19 contact tracing apps have been deployed by both governments and organizations around the globe.
Not all contact tracing apps are equal and an app used by a company to contact-trace its employees while at work can have different objectives than those of an app used by a government to contact-trace its citizens. Any app with tracing functionality should follow best practices when it comes to the collection of data and how that data is stored and used, and there are different rules and regulations relating to this in different parts of the world. This report will analyze 25 popular COVID-19 tracing apps to find out how they do when it comes to security and privacy. However, first, we need to lay out which type of apps we will be looking at and how they work, as well as some of the laws and usage requirements that can shape contact tracing apps.
Government vs private
Tracing apps developed and used by governments and ones used by businesses can be for very different use cases. A government app’s intent is to keep track of who a user has been in contact with and to alert users if they have been near a person infected by the virus. An app provided to employees by their employer may be intended to do the same but in a geofenced area, namely the workplace. As well as this it may be needed to trace an infected user’s movements so that the relevant areas can be disinfected. For the purpose of this report we will not be analyzing apps intended for use by employees solely in the workplace and will focus instead on national apps intended for use by the general public.
GDPR
Tracing apps intended for use in the European Economic Area (EEA) must be in compliance with the General Data Protection Regulation (GDPR). GDPR’s stringent privacy and data protection principles offer a comprehensive, functional blueprint for digital system design and, as such, may be viewed as a benchmark to aim for, even for apps in regions of the world that do not have to comply with the regulations. However, because this is often not the case we will first compare the EEA tracing apps, then the non-EEA apps before finally comparing one set to the other.
How COVID-19 contact tracing apps work
COVID-19 tracing apps use Bluetooth Low Energy (BLE) signals, sent by mobile devices, to keep track of other people and devices the user comes into contact with. If a person they come into contact with tests positive, the app alerts them. Equally, if the user tests positive for COVID-19, the app alerts everyone that they came into contact with.
If done properly, COVID-19 tracing apps have the ability to protect and prevent the spread of the Coronavirus. If not done properly, COVID-19 tracing apps have the ability to put users’ privacy and safety at risk.
COVID-19 tracing app users should expect to be assigned a randomly generated identifier that does not reveal any personal information about them. Furthermore, the app should only be scanning and sending BLE signal data to its servers, but not to any other destinations.
Depending on the use case of a particular app, a range of information may be needed for it to function as intended. For example, if the app is used by a business to trace its employees it may be set up so as to activate and start contact-tracing only within a certain GPS coordinate and conversely to stop once outside those coordinates without recording or sending any information. Furthermore, Wi-Fi data may be needed to justify cleaning/disinfection actions as a result of an infection notification. However, in any scenario, the user must be notified of such data collection. Any data the app is collecting must be clearly and accurately stated in the privacy policy and only collected with the user’s acknowledgment, or with their formal consent where local law so requires. On the other hand, such functionality would not usually be necessary for a nation-wide, publicly available, contact-tracing app
The joint Google and Apple Exposure Notification System, designed to be used by developers of COVID-19 tracing apps, is a framework that does the legwork "for public health authorities to supplement their existing contact tracing operations with technology without compromising on the project’s core tenets of user privacy and security.” While this is a step in the right direction for users' privacy, it seems that few app developers have adopted the framework. Of all the apps we analyzed, we only saw one that used the earlier version of this system.
Testing methodologies
The cloud-based Symantec App Analysis service performed static, dynamic, and behavioral app analysis for nation-wide, COVID-19 tracing apps publicly available from 31 different countries on the iOS and Android platforms. App analysis identifies apps following known security best practices and apps that impact and increase user privacy, security, and risk.
App behaviors impacting privacy, security, and risk:
- Sending location tracking insecurely
- Exposing private data in the cloud
- Using insecure data storage
- Using authentication insecurely
- Sending data to third-party services not directly relevant to the app’s purpose
- Accessing sensitive device data
- Sharing data with advertising networks or analytic frameworks
- Accessing and sharing the user’s contact list or address book
- Accessing the user’s calendar or in-app purchasing
- Identifying the user or the Unique Device Identifier (UDID)
App behaviors that follow best security practices:
- Certificate transparency for specific domains
- Implementing protected confirmation
- All SSL connections use certificate pinning
- Use of a security framework
- Use of NIST NTP servers
- Use of common cryptography libraries
Generally, runtime permission models by Android and iOS protect users from apps collecting private data without their knowledge. That being said, there are some issues with the permission model that complicate privacy. In particular, Android COVID-19 contact tracing apps use Bluetooth technology. Android devices group Bluetooth permissions and location/GPS services together, requiring the app and app developer to request and gain access to GPS locations.
Analysis results
We analyzed COVID-19 tracing apps available to the public from 31 different countries, identifying app behaviors impacting user privacy and security.
Eight of the COVID-19 tracing apps were from countries within the EEA. For these apps we found the following:
- Three of the eight (38%) access device data containing personal information, potentially exposing users’ identities and raising data minimization concerns under the GDPR;
- Two of the eight (25%) fail to protect user data in transit, potentially exposing private data to eavesdroppers and man-in-the-middle (MitM) attacks.
The remaining 23 COVID-19 tracing apps, which were from non-EEA countries, did noticeably worse:
- 15 of the 23 (65%) access device data containing personal information, potentially exposing users’ identities;
- 14 of the 23 (60%) fail to protect user data in transit.
Overall, the diagnosis is grim. Our findings found over half of all countries’ COVID-19 tracing apps access device data containing personal information and fail to protect user data in transit.
Our findings suggest that if you are using a COVID-19 tracing app from a non-EEA country, compared to one from an EEA nation, your risk increases by a factor of two. However, not all non-EEA apps performed quite as badly, as detailed in the following Examples section.
Examples
The COVIDSafe tracing app from the Australian Department of Health hits the security sweet spot when it comes to COVID-19 tracing app. The privacy policy (https://covidsafe.gov.au/privacy-policy.html) clearly explains how and what personal information is collected and aligns with our analysis of the app. Furthermore, the in-app runtime permissions clearly state the reasons for requesting the privileges, as seen when asking for Bluetooth tracking: [{"description": "COVIDSafe exchanges Bluetooth signals with nearby phones running the same app. These signals contain an anonymized ID, which is encrypted and changes continually to ensure your privacy."}]

| COVIDSafe | |
|---|---|
| Platform | iOS |
| Application URL | https://www.health.gov.au/resources/apps-and-tools/covidsafe-app |
| Application name | au.gov.health.covidsafe |
| Application label | COVIDSafe |
| File hash | ab5205600280951e73dee2e40c2aca0b |
| Version string | 1.5 |
| Item ID | 1509242894 |
| Category | Health & Fitness |
| Author | Department of Health, Australian Capital Territory |
| Rating count | 11238 |
Meanwhile, at the other end of the spectrum, StopKorona! is a COVID-19 tracing app for Android and iOS from the Ministry of Health of the Republic of North Macedonia. It claims to be a "mobile app developed based on the best global practices for the prevention and control of the Coronavirus. The app is intended to trace exposure with potentially infected persons, by the detection of the distance between mobile devices/applications by using Bluetooth technology."
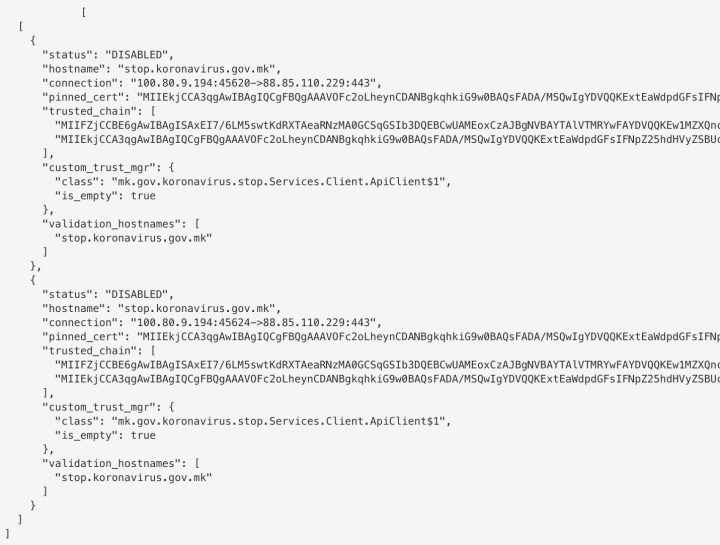
Furthermore, StopKorona! claims that: "The only data related to you is your mobile telephone number, stored on a safe server managed by the Ministry of Health, to prevent the spreading of the virus." We found that the collected data claimed by the Ministry of Health is accurate. What we found inaccurate is the claim that the data is sent securely.
Often we discover in analysis app developers disabling the security or integrity of network connections. This commonly happens when the servers receiving the data are not configured correctly, or the app libraries are not configured correctly. In any case, this disabling of validation of SSL certificate authorities (CAs) is intentional. Furthermore, if you were able to connect to the servers receiving your private data in a browser on the desktop, you would see a broken lock next to the URL showing the connection sending your private data is insecure.
For mobile apps, there is no such lock visible to the user. App developers know this, often using it to pass the test of security while avoiding taking the time to properly and securely configure private data sent over the network.
| StopKorona! | |
|---|---|
| Platform | iOS |
| Application URL | https://stop.koronavirus.gov.mk/en |
| Application name | mk.gov.koronavirus.stop |
| Application label | StopKorona! |
| Category | Social Networking |
| Developer | Ministerstvo za informatichko opshtestvo i administracija Skopje |
| Report | https://api.appthority.com/api/v3/apps/f044d7fff9f94abef2b2c4a378607939/report.json |
| File hash | f044d7fff9f94abef2b2c4a378607939 |
| Version string | 1.1.1 |
| Platform | Android |
| Application URL | https://stop.koronavirus.gov.mk/en |
| Application name | mk.gov.koronavirus.stop |
| Application label | StopKorona! |
| Category | Social Networking |
| Developer | Ministerstvo za informatichko opshtestvo i administracija Skopje |
| Report | https://api.appthority.com/api/v3/apps/6f8133eefc36551d2af64e6a1db05ed8/report.json |
| File hash | 6f8133eefc36551d2af64e6a1db05ed8 |
| Version string | 1.1.0 |
Analysis Tables
Access PII:
Can Access Microphone
Can Access Calendar
Can Access Address Book
Accesses Wi-Fi Info
Accesses Telephony Service
Expose PII:
Sends Data Unencrypted
Disables SSL CA Validation
Data Transport Security Exceptions
App Disabled PFS for Specific Domains
| EEA | Country | Accesses internet | Accesses telephony service | Accesses Wi-Fi info | App disabled PFS for specific domains | Can access address book | Can access calendar | Can access microphone | Data transport security exceptions | Disables SSL CA validation | Sends data unencrypted | Access PII | Expose PII |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| N | Argentina | 1 | N | N | |||||||||
| N | Australia | 1 | N | N | |||||||||
| N | Bahrain | 1 | 1 | 1 | 1 | 1 | Y | N | |||||
| N | Brazil | 1 | 1 | 1 | Y | Y | |||||||
| N | Chile | 1 | N | N | |||||||||
| N | Colombia | 1 | 1 | N | Y | ||||||||
| N | Guatemala | 1 | 1 | 1 | 1 | Y | N | ||||||
| N | India | 1 | N | N | |||||||||
| N | Indonesia | 1 | 1 | 1 | Y | N | |||||||
| N | Israel | 1 | 1 | 1 | Y | N | |||||||
| N | Japan | 1 | 1 | Y | N | ||||||||
| N | Jordan | 1 | 1 | Y | N | ||||||||
| N | Kuwait | 1 | 1 | 1 | Y | N | |||||||
| N | Mexico | 1 | 1 | Y | N | ||||||||
| N | Morocco | 1 | 1 | N | Y | ||||||||
| N | North Macedonia | 1 | 1 | 1 | 1 | 1 | Y | Y | |||||
| N | Punjab | 1 | N | N | |||||||||
| N | Switzerland | 1 | 1 | Y | N | ||||||||
| N | Turkey | 1 | 1 | 1 | 1 | 1 | 1 | Y | N | ||||
| N | Uruguay | 1 | 1 | 1 | 1 | Y | Y | ||||||
| N | Vietnam | 1 | 1 | 1 | 1 | Y | Y | ||||||
| Y | Austria | 1 | N | N | |||||||||
| Y | Denmark | 1 | N | N | |||||||||
| Y | Hungary | 1 | 1 | 1 | Y | Y | |||||||
| Y | Iceland | 1 | N | N | |||||||||
| Y | Ireland | 1 | 1 | Y | N | ||||||||
| Y | Italy | 1 | N | N | |||||||||
| Y | Norway | 1 | 1 | Y | N | ||||||||
| Y | Poland | 1 | 1 | 1 | 1 | Y | Y | ||||||
| Y | Portugal | 1 | N | N | |||||||||
| Y | Spain | 1 | N | N |
| COVID-19 tracing app | Developer | Category | |
|---|---|---|---|
| Aarogya Setu | NATIONAL INFORMATICS CENTRE | Health & Fitness | |
| Alerta Guate | In-telligent Properties LLC | Lifestyle | |
| Alertswiss | Swiss Federal Office of Civil Protection | Reference | |
| BeAware Bahrain | eGovernment Authority Bahrain | Health & Fitness | |
| CoronaMadrid | Comunidad de Madrid | Medicina | |
| CoronApp | Ministerio Secretaria General de la Presidencia | Medical | |
| CoronApp - Colombia | Instituto Nacional de Salud | Health & Fitness | |
| Coronavírus - SUS | Government of Brazil | Medical | |
| Coronavirus Australia | Digital Transformation Agency | Health & Fitness | |
| Coronavirus UY | Agencia de gobierno electronico y sociedad de la informacion | Utilities | |
| COVA Punjab | Government Of Punjab | Health & Fitness | |
| COVID-19 | Electronic Health Administration, Ministry of Health of Vietnam | Medical | |
| COVID-19.eus | Osakidetza | Utilidades | |
| COVID-19MX | INFOTEC, Centro de Investigacion e Innovacion en Tecnologias de la Informacion y Comunicacion | Salud y forma física | |
| COVIDSafe | Department of Health, Australian Capital Territory | Health & Fitness | |
| CUIDAR COVID-19 ARGENTINA | Presidencia de la Nacion Argentina | Medical | |
| Home Quarantine (Kwarantanna domowa) | Ministerstwo Cyfryzacji | Medical | |
| Korona Önlem | T.C. Saglik Bakanligi | Health & Fitness | |
| PeduliLindungi | Kementerian Komunikasi dan Informatika Republik Indonesia | Health & Fitness | |
| Shlonik | The Central Agency for Information Technology | Health & Fitness | |
| Smittestopp | Folkehelseinstituttet | Lifestyle | |
| STOP COVID19 CAT | Generalitat de Catalunya | Medical | |
| StopKorona! | Ministerstvo za informatichko opshtestvo i administracija Skopje | Social Networking | |
| Stopp Corona | Osterreichisches Rotes Kreuz | Medical | |
| המגן - אפליקציה למלחמה בקורונה | Israel Ministry of Health | Health & Fitness |







We encourage you to share your thoughts on your favorite social platform.