Decrypted: With more SolarWinds fallout, Biden picks his cybersecurity team
TechCrunch
JANUARY 21, 2021
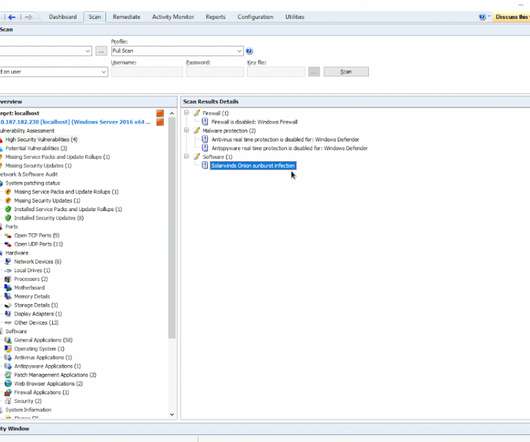
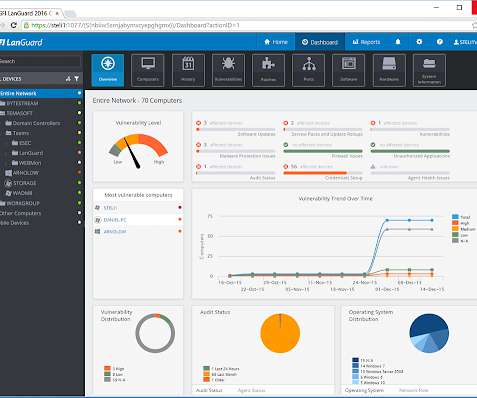
In this week’s Decrypted, we look at the ongoing fallout from the SolarWinds breach and who the incoming president wants to lead the path to recovery. Google says SolarWinds exposure “limited,” more breaches confirmed. It was the same attackers as SolarWinds but using a different intrusion route.



















































Let's personalize your content