INE Security Launches Initiatives to Invest in the Education of Aspiring Cybersecurity Professionals
CIO
AUGUST 23, 2024
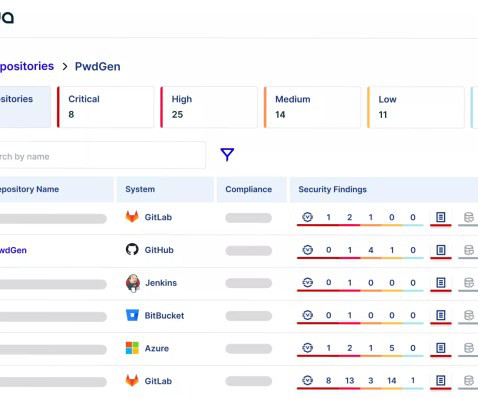
INE Security , a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing campaign to invest in the education of aspiring cybersecurity professionals. million, highlighting the severe economic impact of these incidents.




















































Let's personalize your content