Ross Haleliuk
More posts from Ross Haleliuk
Product-led growth is one of the most commonly discussed topics in the startup world as the market cap of public companies utilizing the growth tactic skyrocketed in recent years.
It’s no different in the cybersecurity space. Why? To find out, I analyzed more than 800 products from over 600 vendors using information from open sources, including Google, Gartner, CB Insights and startup/vendor lists from different sources.
The focus was on security products, not service providers, except companies that have “productized” their services, i.e., offered them as a product package, transparently priced per user, with the ability to sign up online, etc.
Of the 824 products reviewed, 151 can be described as product led.
The below map summarizes the state of product-led growth in the cybersecurity industry.

The categories are intentionally broad; the explanation of what was included in each category is provided below. Some companies have product offerings that fall under multiple categories; I have attempted to reflect these on the map as well.
Companies featured here are at the various levels of PLG maturity: While some have pursued the product-led growth strategy since inception, others have pivoted or are still in the process of making a pivot from being sales-led into PLG.
Trends defining PLG adoption
What’s pushing cybersecurity companies to adopt product-led growth? I observed several PLG-related trends in the cybersecurity space while preparing this market map.
Traditional sales channels have become inaccessible for startups
Chief information security officers (CISOs), leadership teams and midlevel managers have been bombarded with marketing and sales pitches by security vendors. Selling to the highest echelons of security leadership requires a large network, introductions and a large budget for invite-only events, dinners and other entertainment.
These top-down product pitches are not just expensive — they’re ineffective. Hundreds and thousands of vendors attempting to showcase security tools and solutions to security leaders can lead to “vendor overload.”
Security startups have constrained resources and cannot afford to “wine and dine” CISOs, and they don’t have the brand recognition to cut through the noise of vendor overload. With that, entrepreneurs are forced to look for new ways to acquire customers that would allow them to build businesses with reasonable unit economics and the ability to grow. PLG enables companies to lower the customer acquisition cost, bringing the total cost of revenue as close to zero as possible, enabling a hockey stick growth.
Value is a factor defining whether a certain segment can be product led
Not all product categories in cybersecurity have an equal chance to benefit from the unit economics and growth potential PLG enables.
The factors that ultimately define whether a certain segment can be product led are how tangible the product value is and how long it takes for a user to fully realize the value a product in question brings (“time to value”).
First, the product value needs to be well defined and easy to understand. In other words, a person using the product should be able to easily see the difference between “before” and “after.”
Developer-focused products and tools for technical security professionals have a clear edge here as they solve very specific problems their users’ experience, unlike segments like endpoint detection and response (EDR) that sell “security” in a broad sense. Being able to see the product value is not enough; the speed matters just as much. For example, if it takes months to see that the product has prevented ransomware, it’s unlikely people will upgrade to the paid version after 30 days.
One way to communicate the value of the product is to visualize the metrics describing it best. For example, an antivirus could send a daily notification about the number of viruses removed, while a compliance management tool can offer a dashboard with the number of compliance violations detected during the week.
Developer-focused and consumer collaboration tools are leading the PLG wave
In cybersecurity, PLG is more common among companies offering tools for software developers and code security, along with consumer-focused password managers and collaboration tools. It appears that the further away the product is from consumers or dealing with code, the less likely it will be product led.
This is a direct result of the time to value discussed above. Developer-focused products (e.g., Snyk and Twilio) solve a specific, well-understood technical problem for their users. It is easy to see what exactly these products enable (specific technical capabilities), as well as to empirically test and prove whether these capabilities work as intended.
Consumer products leading the space also solve very specific, tangible problems. Password managers, for example, enable users to generate unique passwords for each website (which is well understood to be the right approach to data security) and then store all of their passwords in one place, thereby eliminating the need to remember them.
PLG security products targeting less technical security professionals are just starting to emerge and are less common overall. Even less common are consumer products solving an ephemeral problem of “keeping people secure.” Malwarebytes, which operates in both B2B and B2C segments, is one of the exceptions.
The open source past is shaping the expectations of technical users
Cybersecurity has evolved from an open source mentality. Even today, some of the most used cybersecurity products and solutions are built by volunteers looking to solve a specific security challenge and open to sharing their solutions with others.
Sigma, for example, is a globally adopted generic and open signature format that allows security professionals to describe relevant log events in a straightforward manner. WireGuard is a simple yet fast and modern VPN that became a de facto standard in Linux VPN technology. The list goes on and on; network vulnerability scanning alone can be done with the help of as many as five open source tools — OpenVAS, OpenSCAP, Nmap, Wireshark and Metasploit.
All open source tools are openly built, and most are free (and those that aren’t are transparently priced) because they do not rely on sales teams for distribution. This open source mentality has shaped purchasing expectations of technical buyers: While business buyers (midlevel managers, leadership teams, etc.) are more than happy to attend sales demos and fill out requests for quotes, technical professionals demand the ability to try a product in their home lab, look under the hood and do what they need without any barriers.
Some companies started as open source and then became closed source, so PLG is the go-to-market strategy they evolved from the open source days.
PLG companies are raising the bar for technical security tools
As an extension of the previous point, security professionals like to tinker with and test different security tools, and they expect that they can evaluate the product without having to go through tens of demos and sales calls. Driven by the accessibility of open source, there used to be a perception that open source is easy to access while commercial products are gated.
Companies that embrace product-led growth are raising the bar for technical security tools and therefore changing the expectations. The more commercial security products become product led, the more security professionals will expect the PLG experience.
Companies that do not embrace ideas of openness and transparency will be pushed away from the market. This has already happened in other market segments: If I need a project management and collaboration tool, I can create an account with Asana and get started in seconds without having to talk to anyone. Why would I complicate my life and sign up for a demo of a gated and inaccessible competitive software that promises to solve the same problem?
Sales-led companies are supplementing their efforts with PLG
Traditional, sales-led businesses are starting to realize the power of product-led growth. We are seeing more and more sales-led businesses extending their strategy to PLG to capture a larger slice of the market and allow prospects to try their product. While this trend is likely to continue, it’s important to emphasize a few important points.
I did not find any evidence that sales-led businesses are looking to pivot to product-led growth. Instead, they are supplementing their main customer acquisition channel (sales) with a non-gated product.
Tactically, this means two things. First, product is seen as a channel for sales lead generation as opposed to the change in company mindset or a go-to-market strategy. Second, hiring product managers asked to “be in charge of PLG” can lead to confusion and even clashes between product and sales teams.
Being product-led is much more about the company mindset than it is about the product. This is why it is hard to say from the outside what companies are truly embracing the PLG mindset versus remaining sales-led and simply talking about PLG to get media attention and attract talent.
Growing and amplifying PLG
There are a number of factors that impact the company’s ability to successfully embrace PLG as a strategic mindset. There are several factors that can support or impede the PLG adoption.
Product-led growth is tightly intertwined with community-led growth
Product-led growth heavily relies on word of mouth and intentionally designed growth loops to scale. While not all companies are at the level of PLG maturity that would enable them to design effective growth loops like Slack, Pinterest, SurveyMonkey and similar companies, word of mouth can be amplified by anyone with a deep understanding of communities.
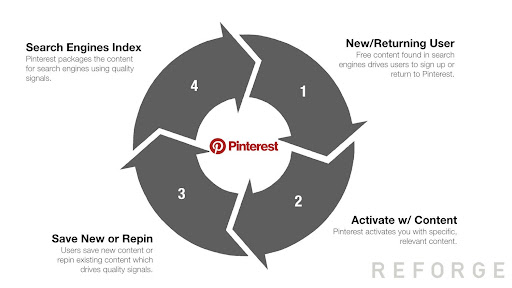
As some product experts highlight, in PLG companies, community-enabled growth can act as a multiplier for a product’s success. Communities can be a great source for product feedback, ideas for improvement and insights about the market direction. Open source projects often use them as a channel for customer support and new user onboarding.
Some examples of PLG companies that leverage community for growth include Tines, Siemplify, Splunk and Elastic. All these companies are investing in building a community — a place where people make connections, grow together and are happy to help one another solve security problems.
PLG requires product talent to lead
Few companies in cybersecurity are being intentional about PLG as their go-to-market strategy. Even fewer are hiring product managers with the mandate to specifically support product-led growth. Snyk, for example, is looking for a VP of Enterprise Sales to “scale and integrate top-down selling motion with product-led growth (PLG) programs to drive strategic relationships within key accounts.” This is an example of both high product maturity and intentional organizational design.
For product-led growth to become commonplace in cybersecurity, there needs to be enough product talent with the right mindset and level of maturity required for PLG. However, cybersecurity is a deeply specialized discipline, so while the specialized security knowledge isn’t mandatory, it does help to shortcut the learning curve.
The irony is that cybersecurity businesses fall victim to a Catch-22:
- Product managers with experience in cybersecurity generally have no experience working in PLG companies (let alone evangelizing product mindset across the organization).
- People making hiring decisions in security companies strongly prefer product managers with a security background as it “helps them to get up to speed quickly.”
The exception is, once again, developer-focused security products because they tend to want two of the three: experience in cybersecurity, experience in developer-focused products, experience in PLG. It’s relatively easy to find product leaders with a “PLG + developer-focused” combination.
Companies that can get out of the short-term mindset and hire PLG leaders without a background in security will set themselves up for success long-term.
The global nature of the security market is fueling PLG
Unlike market segments like financial technology, healthcare or legal tech, cybersecurity does not, by and large, have boundaries requiring it to be heavily localized. Cyber threats are global, and so is the mindset of professionals working in this field. Even compliance requirements such as GDPR, which originate in one part of the world, are soon being adopted globally because of the interconnected nature of global commerce.
Cybersecurity communities and events, from Black Hat and DEF CON to BSides and capture the flag (CTF) competitions, bring together professionals from all over the world to connect, learn and develop new security solutions together.
The global nature of the security market is fueling PLG as it makes it easy for people in any geography to try and adopt a product built on the other side of the planet, without any investments into sales and marketing from the parent company.
Engineering as marketing can act as an amplifier for PLG
A number of cybersecurity companies build tools adjacent to their commercial offerings that can be leveraged at no cost. This approach is known as “engineering as marketing.” Done well, it can also support the PLG as it allows for virality.
An example of a company that does this incredibly well is Moz, the leader in SEO software, which offers a set of free tools — Link Explorer, Keyword Explorer and Domain Analysis, among others
Several PLG companies in security leverage engineering as marketing to amplify their product-led efforts as well, including Security Scorecard and Qualys.
Designing conversion points is an art
The way companies approach the conversion of freemium users into paid customers varies based on their PLG maturity.
Very few high-maturity PLG companies possess a deep enough understanding of the customers, their pain points, needs, wants and perception of the value they assign to specific features and capabilities to design effective conversion points within the product itself. Most low-maturity products have a call to action at different points of the customer journey that directs users ready to convert to the sales team. These companies use the product as the lowest step in their more traditional sales funnel.
Whether the conversion or the upgrade to the higher tier happens organically or it’s assisted by sales, as long as the value is realized by using the product and the decision to upgrade is derived from this realization, I still consider the product to be PLG.
Going beyond PLG
PLG is important but it is never enough.
At a certain stage, PLG companies are required to adopt top-down sales to keep growing.
Companies that started as PLG are eventually forced to adopt top-down sales to grow their revenue past $500 million — $1 billion ARR by leveraging enterprise adoption. The timing of the up-market move is critical, and so is the companywide alignment and the buy-in from a broad range of stakeholder groups, including engineering, product and operations.
Companies with the product-led DNA are able to introduce the enterprise sales function while remaining product driven at their core. Examples of companies that did this well include Slack, Twilio, Auth0 and PagerDuty.
Bessemer Partners has a great guide about introducing enterprise sales to a product-led growth organization.
Product categories
Below is a brief overview of product categories reflected on the market map. These categories should be used to provide a useful level of industry segmentation, not viewed as a perfect way to slice the market. It was developed based on information from open sources, including Google, Gartner, CB Insights and Optiv.
Data protection
Under this category, I looked at products and vendors solving problems in the area of data protection by offering tools that provide data discovery and classification, public key infrastructure (PKI), data loss prevention (DLP), data access governance, electronic discovery, data encryption, data access governance (DAG), file integrity monitoring (FIM), secure collaboration and data sharing, blockchain security, tokenization and database security.
The vast majority of the PLG companies in this space are collaboration and data sharing platforms (Dropbox was one of the pioneers of the PLG approach) and password managers (1Password is valued at $6.8 billion as of 2022). As the work-from-home trend and hybrid work arrangements create new challenges for companies to keep their data safe, we are likely to see rising valuations and more PLG companies attempting to enter this already crowded space.
Risk and compliance
Under this category, I considered products and vendors solving problems in the areas of risk and compliance by offering tools that provide governance, risk and compliance (GRC) and fraud prevention.
Risk and compliance products have historically been sold, not bought. As compliance is evolving from yet another responsibility handled by people in legal into a mature field with specialized professionals, we are likely to see more PLG companies emerging in this space.
Identity management
Under this category, I looked at products and vendors solving problems in the areas of identity management by offering tools that provide digital identity and access management (IAM) and privileged access management (PAM).
Identity management products are generally targeting developers, so the number of PLG products in this segment is higher. PLG has proven to be effective for developer-centered tools (examples include Twilio and GitHub), and security vendors are taking note. M&A deals and valuations in this category are very encouraging as well — consider Okta’s $6.5 billion acquisition of Auth0 in 2021.
Application security
Under this category, I looked at products and vendors solving problems in the areas of application security by offering tools that provide application security testing, software composition analysis, code security and web application firewall (WAF), as well as distributed denial-of-service (DDoS) attack mitigation.
Similar to the identity management segment, this one targets engineers and therefore is well positioned for the PLG disruption. Companies like Snyk (valued at $8.5 billion in 2021) are leading the category.
Security operations
Security operations are the broadest category on the market map. Under this category, I looked at products and vendors solving problems in the areas of security operations by offering tools that provide security infrastructure, vulnerability assessment, and management, orchestration and automation (often referred to as SOAR — security orchestration, automation and response), incident detection and response, security-related change management, security monitoring and operations, as well as threat detection.
There is a large number of PLG products that were categorized in this segment, ranging from open source tools and small startups to large companies. As noted before, it is becoming more and more common for security engineers to play with the product in their home lab and then recommend it at work.
We can see various types of tools here, and the number of products alone is a sign of many more product-led cybersecurity startups to come.
IoT security
Under this category, I looked at products and vendors solving problems in the areas of Internet of Things (IoT) security by offering tools that provide IoT network security, industrial control system (ICS) security and IoT analytics and security.
The global IoT market was valued at $44.46 billion in 2020 and is projected to reach $153.80 billion by 2028. As the use of connected devices increases, so does the potential for cyber threats. The IoT security market segment is going to grow in the coming years and, with that, likely the number of PLG products in this area. There are currently two firms I have identified as taking the PLG approach.
Cloud and SaaS security
Under this category, I looked at products and vendors solving problems in the areas of cloud and SaaS security by offering tools that provide application security, container security, SaaS security, cloud-specific compliance and reporting, cloud micro-segmentation, cloud automation, cloud workload protection (CWP) and cloud access security broker (CASB).
Network security
Under this category, I looked at products and vendors solving problems in the area of network security by offering tools that provide wireless security, secure networking, network access control (NAC), secure web gateways (SWG), SSL visibility/monitoring, distributed denial-of-service (DDoS) attack mitigation, firewalls and software-defined perimeter.
Endpoint security
Under this category, I looked at products and vendors solving problems in the areas of endpoint detection and response (EDR and XDR, which stands for extended detection and response), endpoint protection, application control and intrusion prevention (intrusion prevention system, or IPS for short).
This space has historically been dominated by large enterprises, and even newer EDR players like CrowdStrike and Cybereason have chosen a sales-led approach.
All four product-led players in this area are unique in some way: LimaCharlie is a security infrastructure-as-a-service provider that covers endpoint security, among other things; Cyvatar is a security service provider that packages its offering as a product; Elastic is described as a “search company that builds self-managed and SaaS offerings for search, logging, security, observability and analytics use cases,” so endpoint security isn’t their main focus; and Malwarebytes is an anti-malware software.
Data center
Under this category, I looked at products and vendors solving problems in the area of data center security by offering tools that provide email security, deception, secure storage, secure platform, domain name system (DNS), dynamic host configuration protocol (DHCP) and IP address management (IPAM) security.
Given the technical nature of the buyers in this segment, it is surprising that only three products were identified as PLG.
Methodology and parameters used for evaluation
Product-led growth is more about the mindset than it is about the product, and it’s not always easy to say from the outside what companies are pursuing this strategy. There are, however, some indicators about who is not doing it. Companies that do not make their pricing public, require a mandatory sales demo or prevent the ability to get started without having to sign a contract are not at all likely to be product-led.
Bessemer describes 10 product-led growth principles:
- Build product as its own self-serve distribution vehicle.
- Deliver a eureka moment instantaneously.
- Focus on creating value instead of extracting value.
- Center the product universe on the end user.
- Establish a clear initial entry wedge.
- Generate virality through network effects.
- Employ a transparent pricing model.
- Design straightforward packaging based on intuitive gates.
- Embed customer success levers.
- Infuse a product-led philosophy throughout the organization.
With that, below are the factors I took into consideration when evaluating the products for the market map:
- Freemium: Does the product have a free tier that would allow users to understand the value proposition of the free offering and the additional value they would realize if they were to upgrade to the paid version?
- Free trial: Does the product have a free trial that would allow users to realize the full value of the product before they start paying?
- Transparent pricing: Is the pricing fully transparent, allowing people to evaluate the cost without having to talk to the sales team or request a quote?
- Low barrier to entry: Are people able to get started without having to talk to the sales team or jump over other barriers to adopt the product?
There is a medium degree of subjectivity when it comes to assessing these factors for products with low PLG maturity because many are less definitive than simply “yes” or “no.” If your PLG company or a product you know is missing, feel free to add a comment here or ping me on LinkedIn.































Comment