Given the rapidly evolving technological landscape and the increasing sophistication of cyberattacks, organizations need stronger and more robust defenses. Unfortunately, your antivirus and firewall may not cut it in this day and age.
In this blog, we’ll take a broader look at cybersecurity solutions in three key areas that can help you build a solid foundation for overall IT security.
Endpoint Security
Endpoint security is the process of protecting individual devices with the broader aim of securing the network and the data of the organization. In any given organization, endpoints are on the front line of the security war. With IT professionals required to monitor and manage hundreds of thousands of endpoints across multiple networks, the chances of missing security vulnerabilities increase exponentially.
Mentioned below are endpoint security solutions you should definitely consider for comprehensive endpoint protection:
- Endpoint Protection Platform: Cyberthreats are constantly evolving. Simple antivirus and antimalware solutions are no longer enough to prevent targeted and zero-day attacks. To address the current threatscape, your organization needs a comprehensive Endpoint Protection Platform (EPP) that has the following capabilities:
- Preventing file-based malware attacks
- Detecting malicious activities
- Providing the investigation and remediation capabilities needed to respond to dynamic security incidents and alerts.
An EPP is usually an integrated suite of security technologies, such as antivirus/antimalware, intrusion prevention, data loss prevention and data encryption, to detect and prevent a variety of threats at the endpoint.
- Endpoint Detection and Response (EDR): EDR differs from traditional antivirus and antimalware. It takes a proactive approach by not only detecting suspicious activity and malware, but also by keeping the network safe by containing threats to an endpoint in case of an incident (read more about EDR).
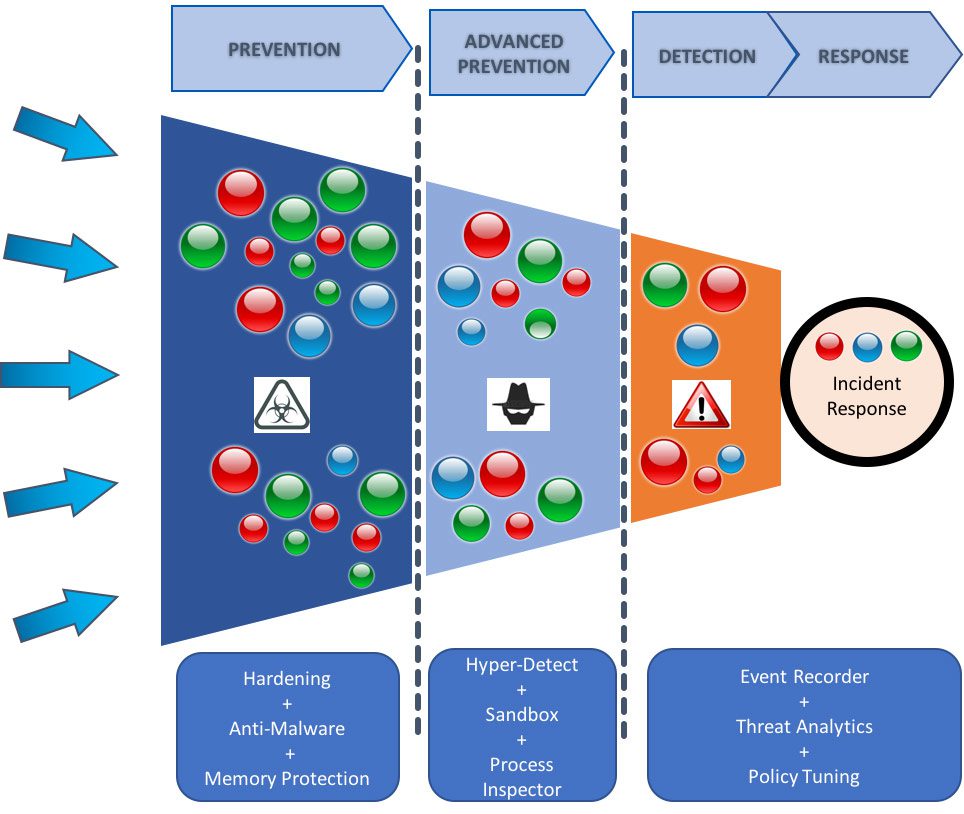
EDR tools protect endpoints by monitoring events, gathering data and analyzing it to reveal potential cyberthreats and issues. They detect anomalies in endpoints by identifying rare processes, risky occurrences and strange connections, which are mostly flagged based on baseline comparisons. To implement EDR in your organization, you could consider tools such as Bitdefender, Webroot or ESET.
Network Security
Keeping your network secure is a very challenging task. There is no fool-proof method of preventing threat actors from invading your network. However, you can inhibit exfiltration efforts and prevent cybercriminals from breaching your organization data by monitoring network anomalies.
To detect anomalies, network security tools first need to understand and define your network’s usual behavior. They can then look for anomalous network behavior, as in, something that deviates from the usual pattern of activity. This includes increased network traffic volume, excess bandwidth utilization, increased number of DNS requests or open TCP connections.
Monitoring network anomalies enables network security tools to detect and prevent lateral movement (techniques that threat actors use to progressively move through the compromised network in search of valuable data) of cyberattackers.
To keep your network secure, you can implement tools such as WatchGuard Network Security, Qualys or Network Detective (RapidFire Tools).
User-Oriented Security
User-oriented security solutions detect user-activity anomalies such as unauthorized logins, privileged access misuse and other malicious activities.
While malicious activities by authorized users, such as theft of intellectual property or security information, can be detected by using insider threat detection tools, thwarting employee negligence involves a more proactive approach of periodically training employees in security awareness. This can include training for phishing attacks based on social engineering strategies, for example.
User-oriented security tools, such as Cyber Hawk (RapidFire Tools), Dark Web ID (ID Agent) and BullPhish ID (ID Agent), enable you to detect suspicious user activity, proactively monitor the Dark Web for an organization’s compromised or stolen credentials, and provide employee security awareness training respectively. (Learn more about Dark Web monitoring).
Conclusion:
A complete cybersecurity solution requires a number of tools that cover the many different aspects of this space. Look for tools that can be integrated with your endpoint management solution to make security management more efficient. Manage endpoints, AV/AM clients, backup and more from the same console.
To learn about Kaseya’s cybersecurity solutions, download the feature sheet here.





