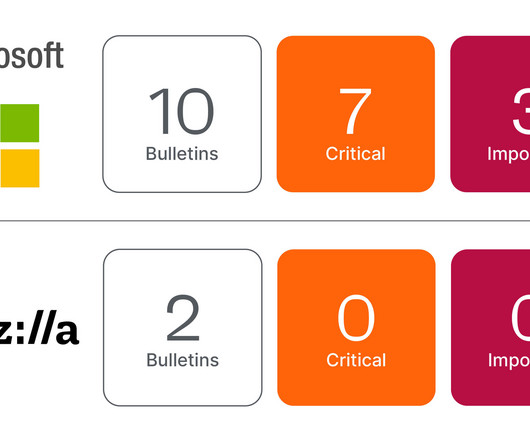
Microsoft’s October 2023 Patch Tuesday Addresses 103 CVEs (CVE-2023-36563, CVE-2023-41763)
Tenable
OCTOBER 10, 2023
An unauthenticated, remote attacker could exploit this vulnerability using social engineering in order to convince a target to open a link or download a malicious file and run it on the vulnerable system. Alternatively, an attacker could execute a specially crafted application to exploit the flaw after gaining access to a vulnerable system.






















Let's personalize your content