HackerEarth introduces Full-stack Assessments at Hire10(1) Conference
Hacker Earth Developers Blog
OCTOBER 7, 2020
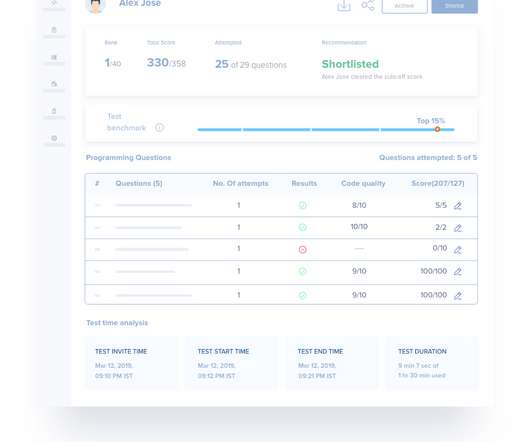
HackerEarth has just announced the addition of full-stack assessments to help recruiters efficiently evaluate the coding skills of full-stack developers. increased by 206% between 2015-2018. Features Coming Soon: Automated code quality score. Organizations are increasingly looking to recruit full-stack developers.














































Let's personalize your content