PopSQL aims to be a modern data team’s best friend
TechCrunch
FEBRUARY 9, 2022
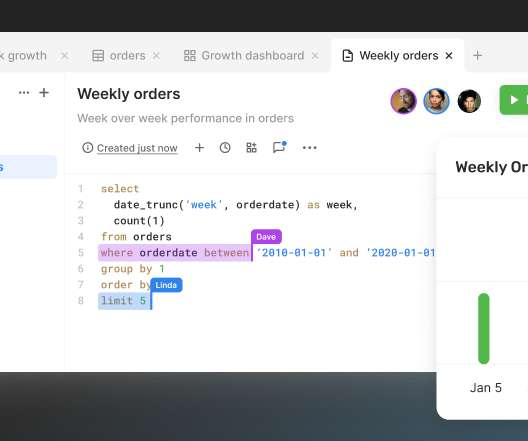
But what you often have to do next is save the query somewhere, send it to someone else so they can review it and make sure it’s good or if you make a data table or charts, have an easy way to share that.”. “The most basic task is connecting to the database, writing the query, then getting the results,” he added. PopSQL raised a $3.4











































Let's personalize your content