How VPR Helped Prioritize the Most Dangerous CVEs in 2019
Tenable
APRIL 30, 2020
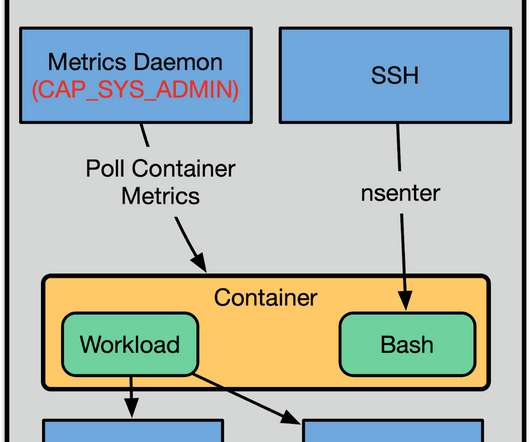
How do VPR and CVSS compare when assessing the most dangerous CVEs in 2019? Two weeks ago, we kicked off a blog series on vulnerability priority rating (VPR), with a post focused on the characteristics of VPR that differentiate it from CVSS. Verint identified a list of the most exploited old CVEs by APT in 2019. Let’s find out.














































Let's personalize your content