Developers Skill Assessment Software: Testing Beyond the Technical
Hacker Earth Developers Blog
NOVEMBER 17, 2022
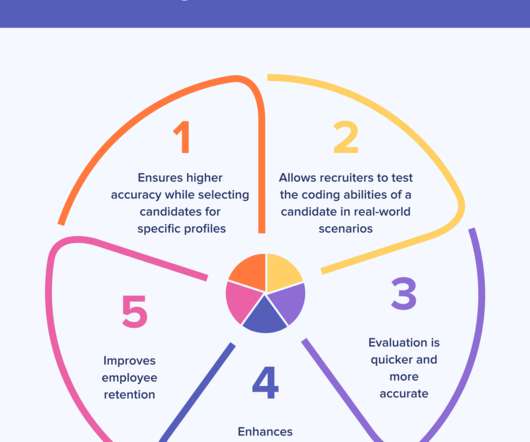
Skill assessment software has become the new buzzword in the software development industry. Recruiters are looking for highly skilled candidates to handle their software development duties. As a result, the demand for talented software developers is witnessing unprecedented growth.

















































Let's personalize your content