Agentless Workload Scanning Gets Supercharged with Malware Scanning
Prisma Clud
JUNE 22, 2023
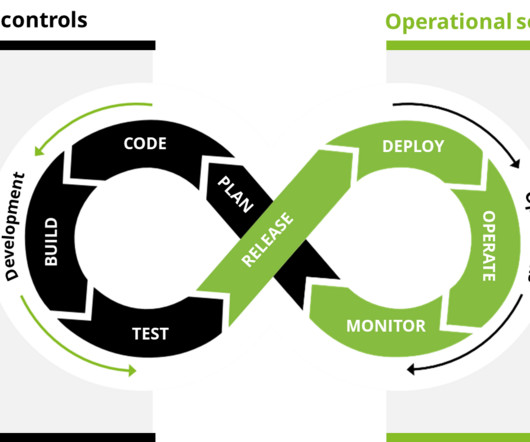
Using WildFire in 2021 to analyze malicious files, our threat research team discovered a 73% increase in Cobalt Strike malware samples compared to 2020. The speed, volume and sophistication of modern malware attacks has made them more difficult to detect. Teams need the ability to set up cloud security in a few clicks.




















































Let's personalize your content