How to expose events to third parties on the public internet
Xebia
JUNE 8, 2022
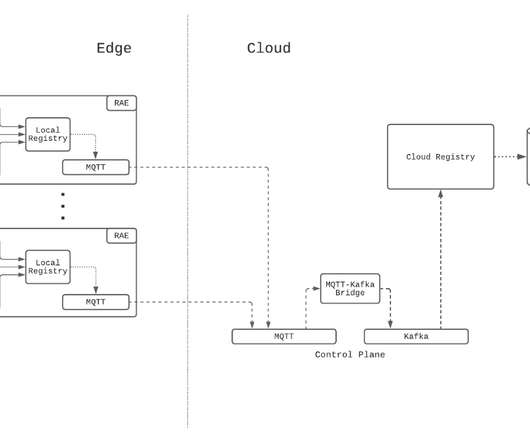
Server-Sent Events are a great way to expose events to trusted third parties over the public internet. In this blog we will explore five ways to expose your existing messaging middleware to the internet: direct, polling, websockets, webhooks and server-sent events. Server-Sent Events. Direct connection. Websockets.


















































Let's personalize your content