CVE-2023-20198: Zero-Day Vulnerability in Cisco IOS XE Exploited in the Wild
Tenable
OCTOBER 16, 2023
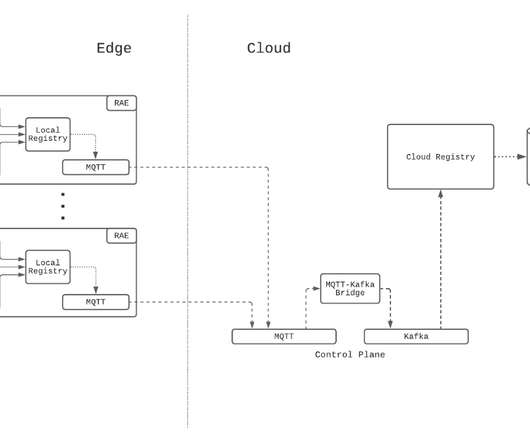
Background On October 16, Cisco’s Talos published a blog post warning of a zero-day vulnerability in the Web User Interface (Web UI) feature of Cisco IOS XE software that has been exploited in the wild by unknown threat actors. At the time their blog was released, it was not known how they were able to do so.









































Let's personalize your content