More connected, less secure: Addressing IoT and OT threats to the enterprise
CIO
NOVEMBER 14, 2023
Weak authentication and authorization: One of the foremost vulnerabilities in IoT deployments stems from inadequate authentication and authorization practices. These issues are akin to leaving the front door to your digital infrastructure unlocked.












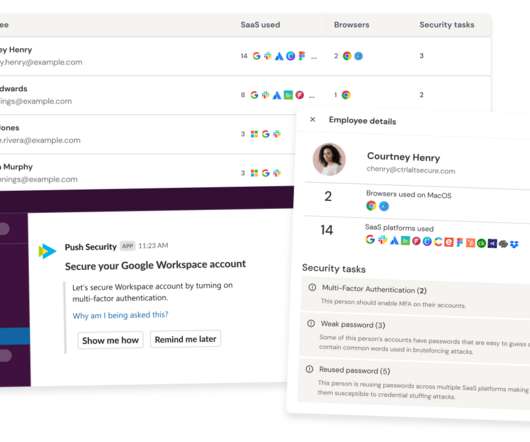









































Let's personalize your content