pdflayer API Review – HTML to PDF Conversion API for Developers
The Crazy Programmer
APRIL 6, 2021
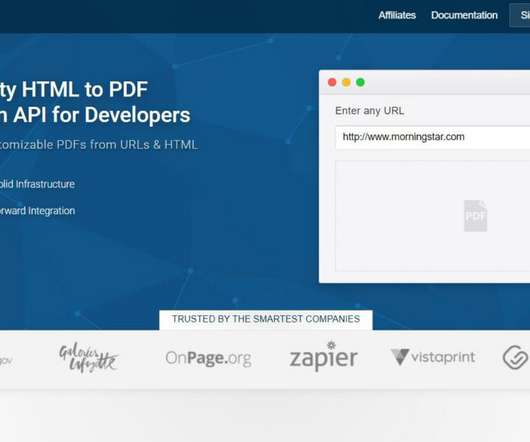
pdflayer combines several powerful PDF engines based on browsers running stalwart operating systems. API Access Key and Authentication. A base endpoint URL is available where users need to attach the API access key for authenticating pdflayer API. API Error Codes. Robust PDF Engine. Powerful CDN.




















































Let's personalize your content