Cluster Management in Cassandra: Achieving Scalability and High Availability
Datavail
DECEMBER 26, 2023
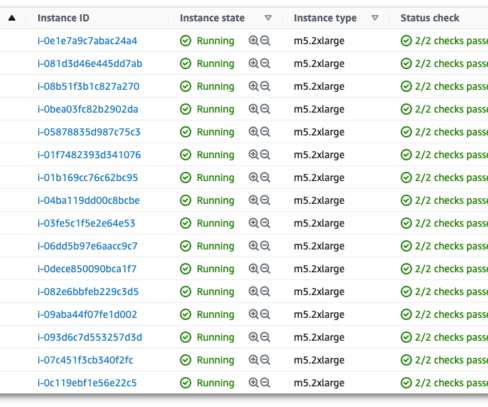
For example, on Ubuntu, you can use the following commands: Once Cassandra is installed, edit the `Cassandra.YAML configuration file located in the `/etc/cassandra/` directory: In the `Cassandra.YAML file, update the following properties to configure the new node: cluster_name: Set the name of your Cassandra cluster.






































Let's personalize your content