Enterprise Storage Arrays and NVMe
Hu's Place - HitachiVantara
AUGUST 29, 2018
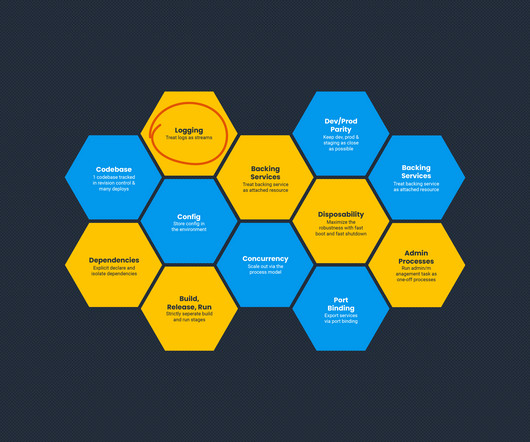
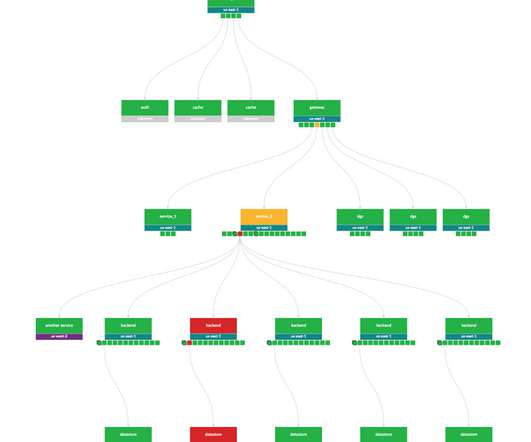
The hot topic in storage today is NVMe, an open standards protocol for digital communications between servers and non-volatile memory storage. NVMe was designed for flash and other non-volatile storage devices that may be in our future. Scalable enterprise NVMe storage arrays will likely require a fabric on the backend.






































Let's personalize your content