Generative AI: 5 enterprise predictions for AI and security — for 2023, 2024, and beyond
CIO
OCTOBER 25, 2023
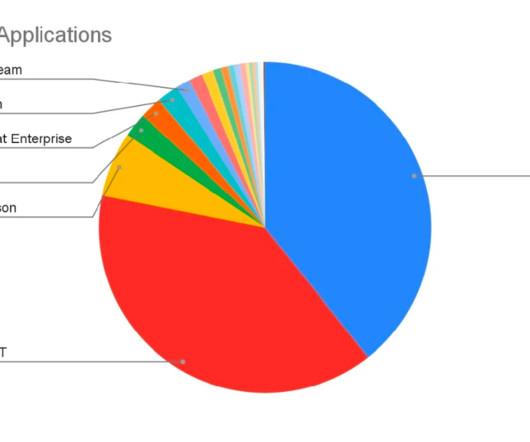
Zscaler The risks of leveraging AI and ML tools As we discussed in a recent blog , the risks of using generative AI tools in the enterprises are significant. The release of intellectual property and non-public information Generative AI tools can make it easy for well-meaning users to leak sensitive and confidential data.











































Let's personalize your content