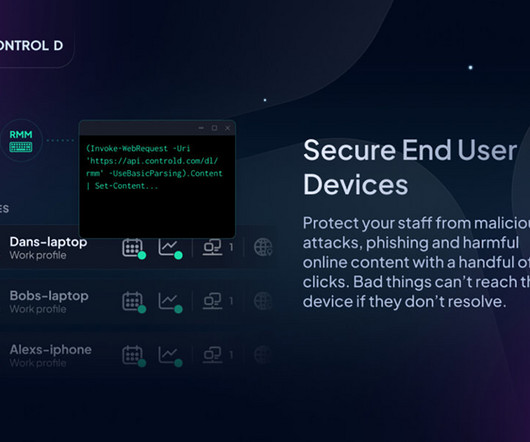
Control D Launches Control D for Organizations: Democratizing Cybersecurity for Organizations of All Sizes
CIO
MARCH 19, 2024
This modern DNS service democratizes cybersecurity, making it accessible to businesses of every size, from budding start-ups to late stage SMBs and MSPs. Malware Blocking : Protecting business continuity against malicious threats with state-of-the-art detection techniques, all built in-house.















































Let's personalize your content