Network Security: A Top Priority for Healthcare Organizations
Firemon
FEBRUARY 14, 2024
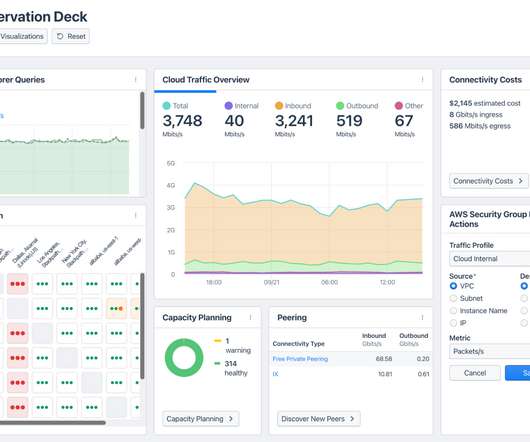
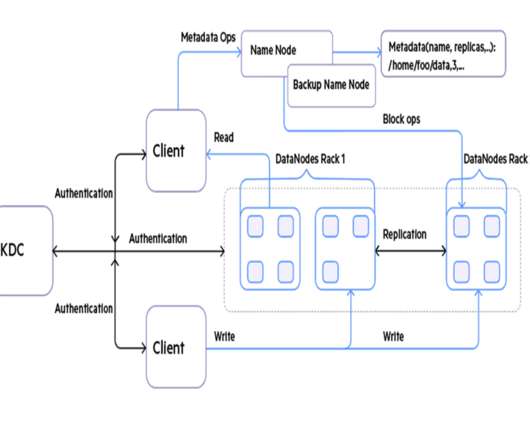
How is FireMon Better Book a Demo Healthcare companies have a responsibility to protect sensitive patient data and ensure compliance with regulations like HIPAA. FireMon’s solutions provide enhanced network security, compliance management, and real-time visibility and control. Why Act Now? Why Choose FireMon? Why Act Now?
































Let's personalize your content