Unlocking Kubernetes Innovation Through Simplified Cloud Security with Tenable
Tenable
MARCH 19, 2024
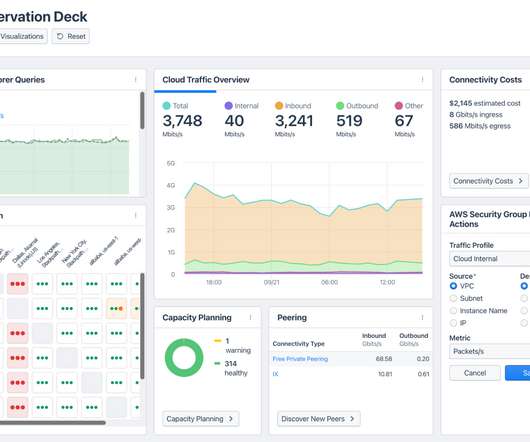
Clusters often run the most critical workloads to a company’s business and may also have access to the organization's most sensitive resources including confidential company and customer data. As a CNAPP solution, it analyzes all components of the cloud infrastructure for misconfigurations, vulnerabilities and permissions risk.




































Let's personalize your content