Are You Ready for Cloud Regulations?
CIO
JULY 13, 2022
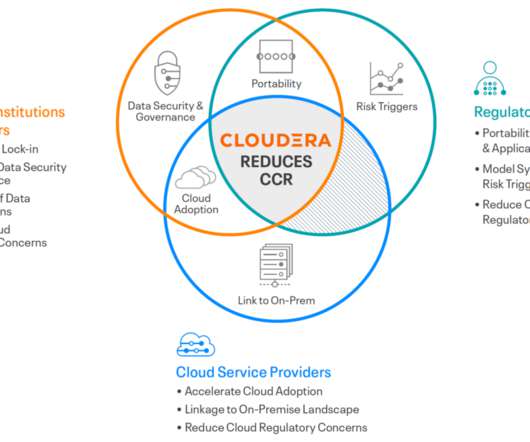
The paper is a proposal to enable oversight of third parties providing critical services to the UK financial system. The proposal would grant authority to classify a third party as “critical” to the financial stability and welfare of the UK financial system, and then provide governance in order to minimize the potential systemic risk.





























Let's personalize your content