Sharing Responsibility for Data Security in the Cloud
CIO
AUGUST 25, 2022
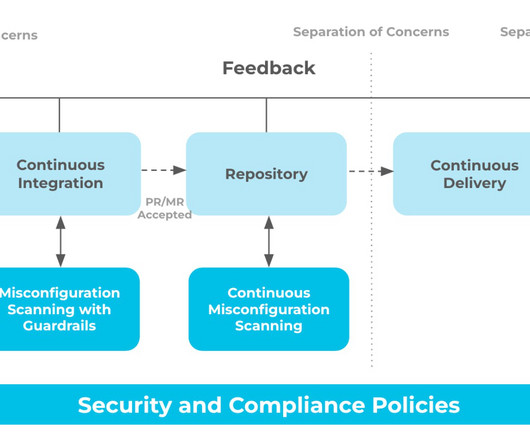
As organizations shape the contours of a secure edge-to-cloud strategy, it’s important to align with partners that prioritize both cybersecurity and risk management, with clear boundaries of shared responsibility. The security-shared-responsibility model provides a clear definition of the roles and responsibilities for security.”.




















































Let's personalize your content