SASE success: Avoid confusion and embrace a single-vendor solution
CIO
NOVEMBER 2, 2023
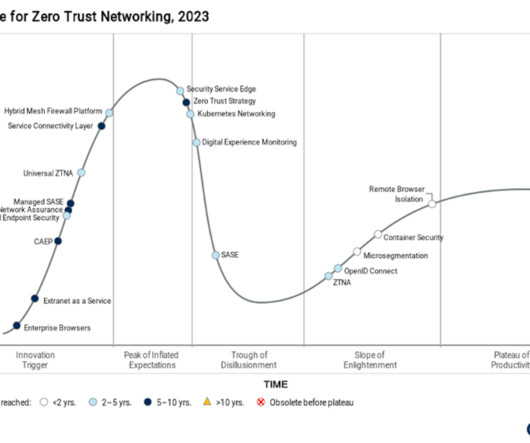
They wrote that “SASE is in the Trough of Disillusionment, due to exaggerated marketing by many technology vendors.” Training is a lot quicker and easier if organizations use a single-vendor approach because all the SASE components should work seamlessly together and can be managed from the same console with unified agent/client.





























Let's personalize your content