Zededa lands a cash infusion to expand its edge device management software
TechCrunch
JULY 21, 2022
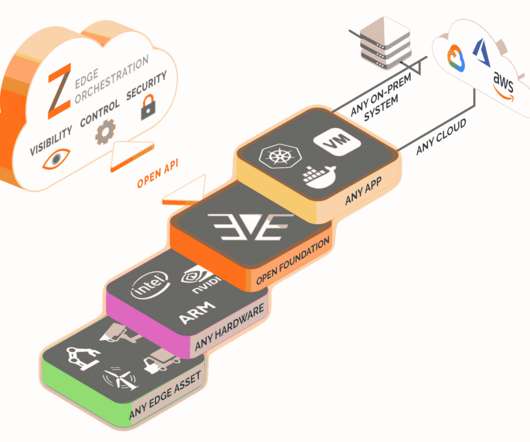
The only successful way to manage this type of environment was for organizations to have visibility across all the hardware, applications, clouds and networks distributed across their edge environments, just like they have in the data center or cloud.” ” Some research bears this out. Image Credits: Zededa.













































Let's personalize your content