Shifting the Paradigm: Why the Cyber Insurance Industry Should Focus on Preventive Security
Tenable
MAY 13, 2024
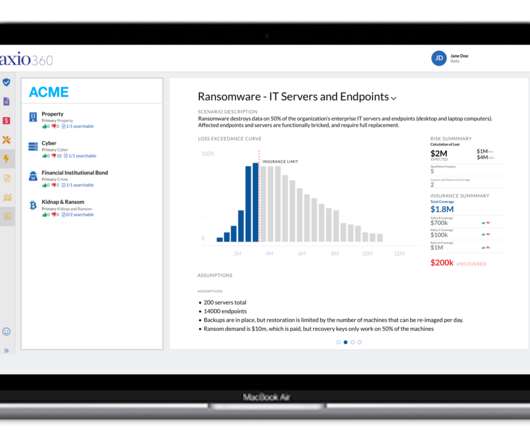
Does your organization currently have a cyber insurance policy? Without it, you are missing a critical piece of a holistic security strategy. With increased cyberattacks and expansion in cloud and digital operational technology (OT) assets, organizations face significant costs during and after breaches.





















































Let's personalize your content