App Control for Linux Opens Up a Whole New World
Ivanti
OCTOBER 28, 2021
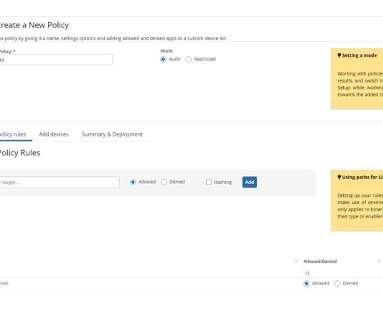
But with the introduction of Ivanti App Control for Linux, we are opening up a whole new world of possibilities. Ivanti Application Control for Linux brings the major benefits of App Control for Windows to Linux environments. It provides for: Policy-Driven Allowed and Denied Lists. Policy-Driven Allowed and Denied Lists.











































Let's personalize your content