HCRootkit / Sutersu Linux Rootkit Analysis
Lacework
SEPTEMBER 23, 2021
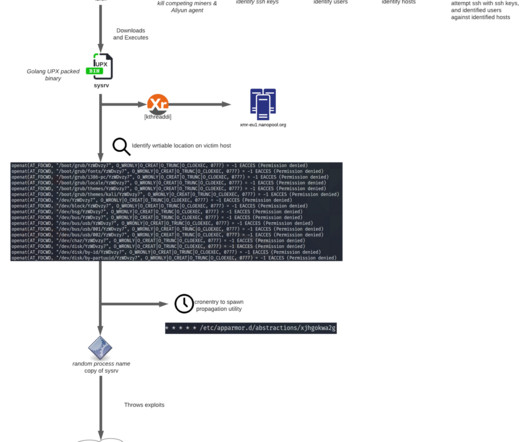
Jared Stroud, Tom Hegel Cloud Security Researchers – Lacework Labs Key Points Lacework Labs identified new samples and infrastructure associated with HCRootkit / Sutersu Linux rootkit activity, building-off its recent initial identification from our colleagues at Avast. These files compromise a host [.].












































Let's personalize your content