ELF of the Month: New Lucky Ransomware Sample
James Condon
Director of Research, Lacework Labs
Photo by Kiki Wang on Unsplash
News broke in late November 2018 about a ransomware variant dubbed Lucky Ransomware that targets both Linux and Windows platforms. A recent sample of the ransomware module was uploaded to VirusTotal in mid-December 2018 with some different characteristics than previously reported samples. In this month’s edition of ELF of the Month, we take a look at this new sample.
Lucky Ransomware Background
Lucky Ransomware was first reported by SANGFOR and NSFOCUS in late November and early December 2018. It is detailed as a variant of Satan ransomware and has both a Windows and Linux version.
The malware is a module in nature with three major components:
- Propagation module
- Ransomware module
- Coinmining module
The malware attempts to propagate via scanning the local subnet for the following vulnerabilities:
- JBoss deserialization vulnerability (CVE-2013-4810,CVE-2017-12149)
- JBoss default configuration vulnerability (CVE-2010-0738)
- Tomcat arbitrary file upload vulnerability (CVE-2017-12615)
- Tomcat web admin console backstage weak password brute-force attack
- WebLogic arbitrary file upload vulnerability (CVE-2018-2894)
- WebLogic WLS component vulnerability (CVE-2017-10271)
- Windows SMB remote code execution vulnerability (MS17-010)
- Apache Struts 2 remote code execution vulnerability (S2-045)
- Apache Struts 2 remote code execution vulnerability (S2-057)
- Spring Data Commons remote code execution vulnerability (CVE-2018-1273)
In addition to this, the malware looks to crack weak passwords on Linux hosts.
The ransomware module encrypts files by file extension while whitelisting a number of directories. It names the files with the extension “.lucky” and leaves a ransom note in a file names “How_To_Decrypt_My_File”.
Lastly, the coinmining module is the open-source Monero miner XMRig.
New Sample Details
On December 13th, 2018, a sample of the ransomware module was uploaded to VirusTotal. At the time of this writing it has been submitted 33 times by four submitters. This sample triggers 16 AV detections, two of which identify the sample as Lucky ransomware in the malware family name.
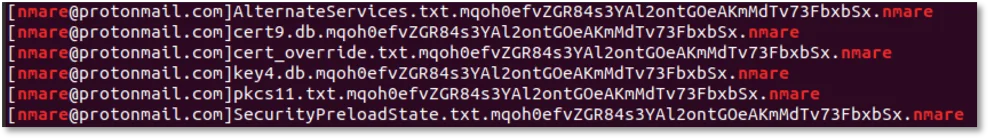
When this sample runs it does a couple things differently. First, it names the encrypted files differently:
“[nmare@protonmail.com]<filename>.<string>.nmare” as opposed to “[nmare@cock.li]<filename>.<string>.lucky”
Figure 1. File listing of encrypted files.
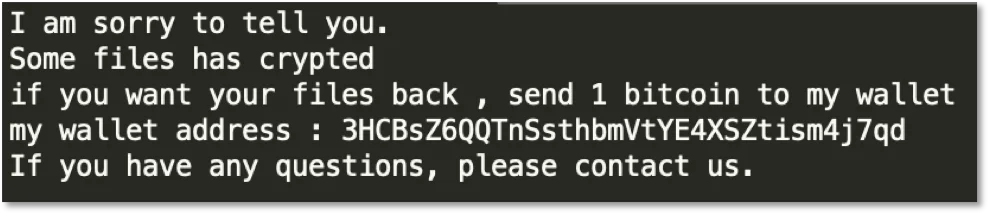
The ransom note is named “How_To_Decrypt_My_File” as opposed to “_How_To_Decrypt_My_File”.
The ransom note contains the same Bitcoin wallet address however the email address has been updated (same as the email in the encrypted filename).
Figure 2. Ransom note.
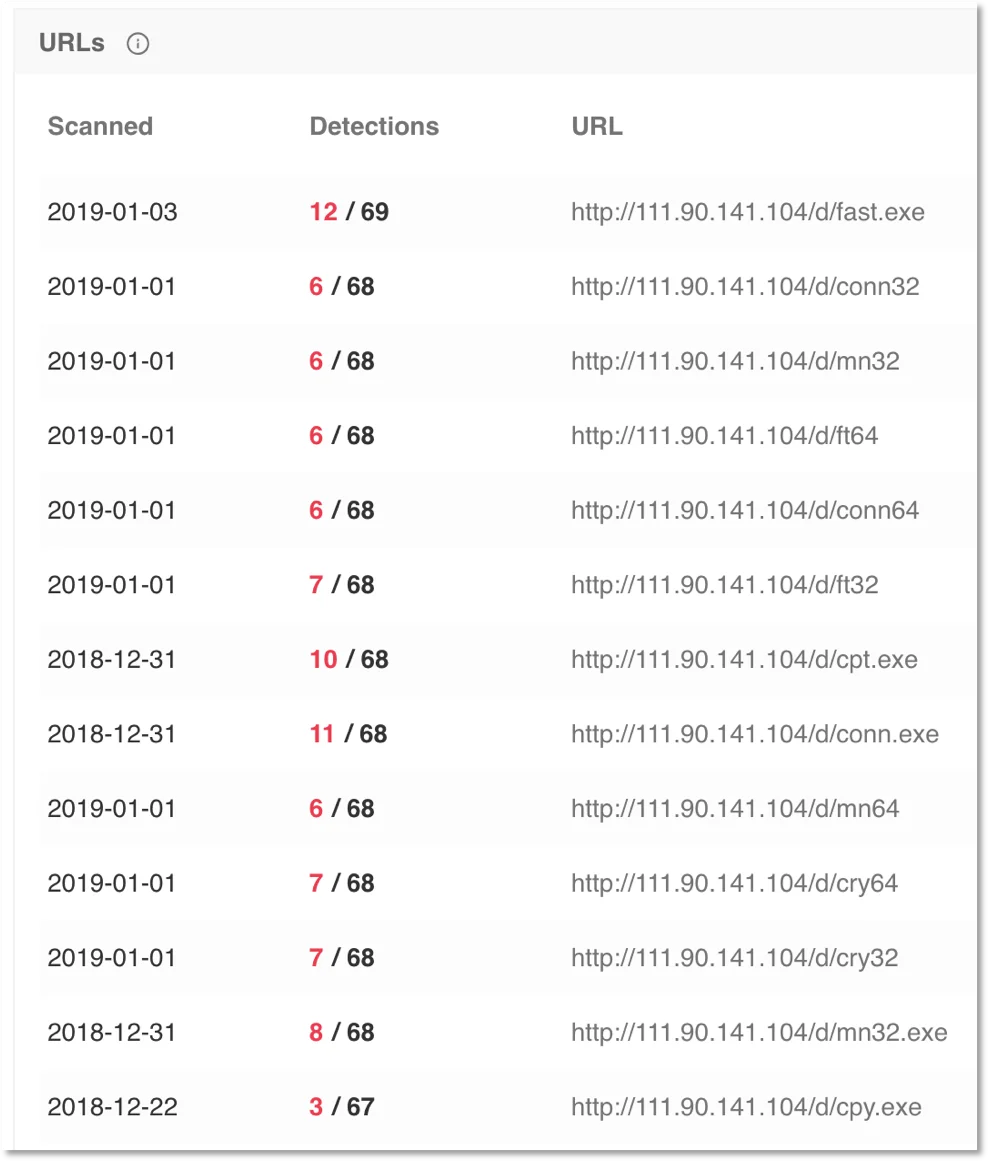
Additionally, there is a new command and control IP, 111.90.141.104. Looking at the IP in VirusTotal you can see a number of URLs containing the modules associated with Lucky Ransomware.
Figure 3. Listing of scanned URLs associated with 111.90.141.104.
Conclusion
The command and control IP for this sample is still active. We expect to see more updates and new samples in the future. For preventative measures update vulnerable versions of software that is targeted by the propagation module, block command, and control infrastructure detailed in this blog and the referenced blogs, and ensure your systems have proper backups in the event of a ransomware infection.
Detection in Lacework
Lacework will detect the following IOCs via File Integrity Monitoring (FIM) and network connection monitoring. Additionally, Lacework alerts on anomalous processes, user activity, and network communications.
IOCs
SHA256 Hashes
IP Addresses
111.90.141.104
URLs
Categories
Suggested for you