K8s Network Policy Automation in Falco Talon
Dzone - DevOps
FEBRUARY 14, 2024
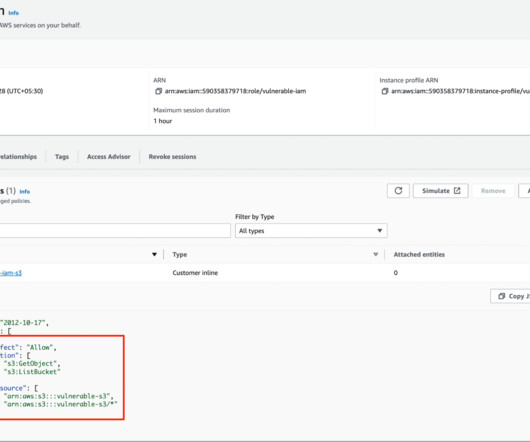
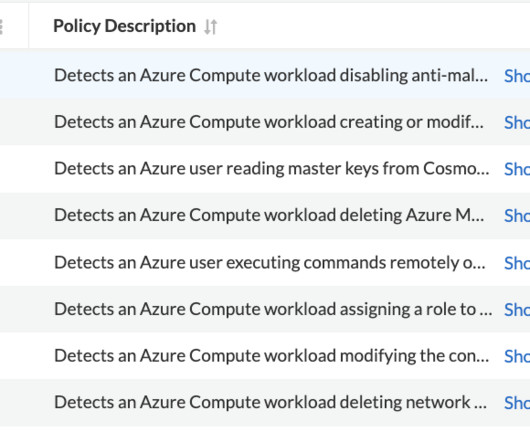
Setting up robust network security in Kubernetes is a challenge that demands both precision and adaptability. NetworkPolicy offers the potential for highly specific network configurations, enabling or blocking traffic based on a comprehensive set of criteria.


















































Let's personalize your content