Masten Space Systems to develop a GPS-like network for the Moon
TechCrunch
JULY 13, 2021
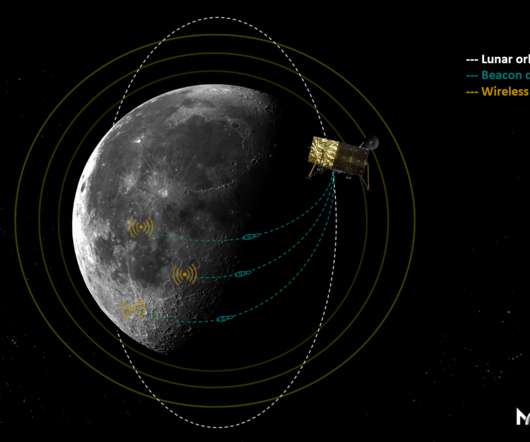
To some extent, it makes sense that a shared navigation network has never been established: humans have only landed on the Moon a handful of times, and while there have been many more uncrewed landings, lunar missions still haven’t exactly been a regular occurrence. Image Credits: Masten Space Systems (opens in a new window).














































Let's personalize your content