Difference between MAC Address and IP Address
The Crazy Programmer
SEPTEMBER 17, 2021
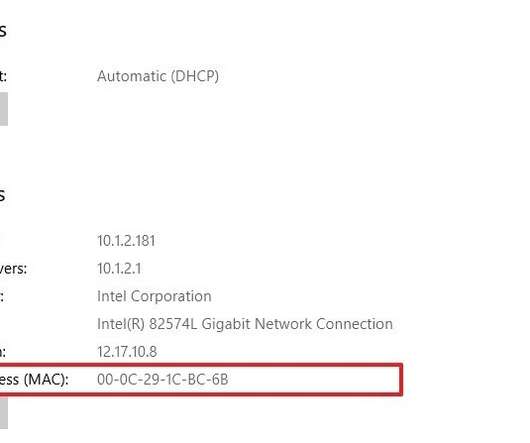
In addition to being known as a physical address, the media access control (MAC) address may be used to identify a device to other devices on the same local network. In order for a network packet to reach its destination, it must have both addresses. It consists of a 48-bit or 64-bit address linked with the computer network adapter.









































Let's personalize your content