Upgrade to Windows 11 with Ivanti Neurons for MDM
Ivanti
APRIL 11, 2024
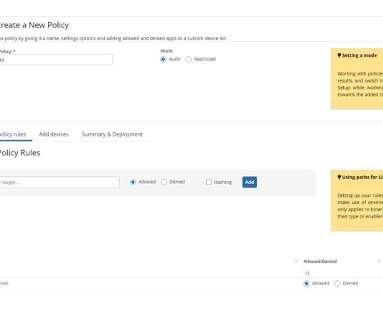
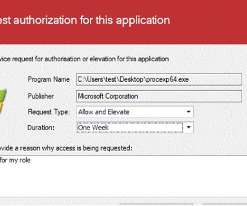
With support for Windows 10 ending on Oct. 14, 2025, users are faced with deciding how and when they wish to upgrade to Windows 11. Since some old devices won’t be able to upgrade to Windows 11, new devices must be purchased. Your organization might be ready to upgrade to Windows 11 or need to plan for it.


















































Let's personalize your content