Top 10 barriers to strategic IT success
CIO
APRIL 29, 2024
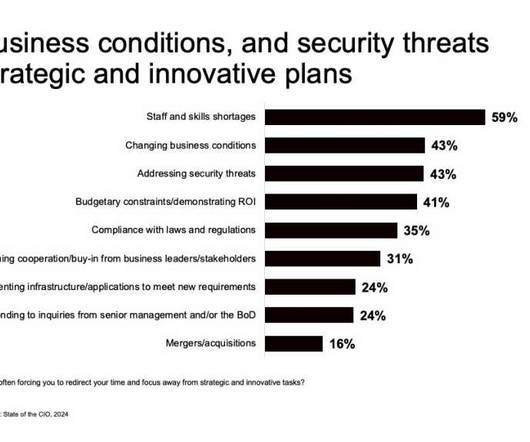
When asked which challenges most often force IT to redirect time and focus away from strategy and innovation tasks, CIOs most commonly cited staff and skills shortages, changing business conditions, and addressing security threats. Tech debt and legacy tech Technical debt and legacy tech are both big speedbumps.



















































Let's personalize your content